How to use buffer overflow to modify function pointer value?

Using Buffer Overflow to Modify Function Pointers | Easy TutorialПодробнее

How to use buffer overflow to modify function pointer value?Подробнее

DEF CON 26 - zerosum0x0 - Demystifying MS17 010 Reverse Engineering the ETERNAL ExploitsПодробнее
#38 Buffer Overflows | Introduction to Operating SystemsПодробнее

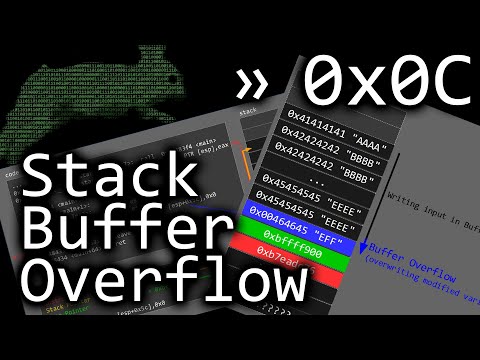
First Stack Buffer Overflow to modify Variable - bin 0x0CПодробнее
Binary Exploitation, Heap-Based Buffer Overflow - Overwrite Function PointerПодробнее
Protostar stack1 - Buffer overflow to change variableПодробнее
Buffer Overflows Part 1 - Jumping to Local FunctionsПодробнее

Buffer Overflow Vulnerability Exploit | Malayalam | Using Function PointerПодробнее

#4 Change program flow - Buffer OverFlow protostar stack3 - binary exploitation شرح بالعربيПодробнее

Function Calls and Buffer Overflows: ASU's Hacking Club Meeting 12/1/21Подробнее
Developing a Tool to Find Function Pointers on The Heap | Ep. 10Подробнее

How They Hack: Buffer Overflow & GDB Analysis - James LyneПодробнее
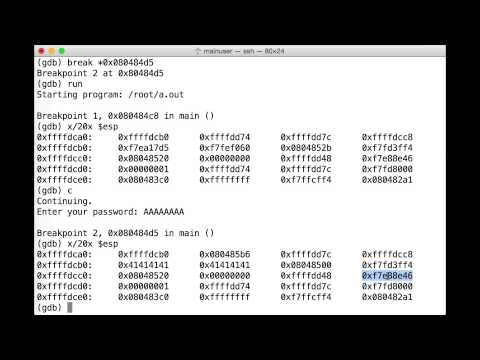
How to exploit a buffer overflow vulnerability - PracticalПодробнее
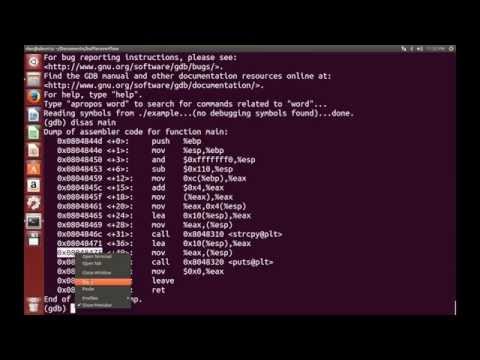
Buffer OverflowПодробнее

Buffer Overflow 101: Ep 1 - x86 Memory FundamentalsПодробнее
Global variable Buffer Overflow to leak memory - 34C3 CTF readme_revenge (pwn)Подробнее

DEF CON 8 - Greg Hoglund - Advanced Buffer Overflow TechniquesПодробнее
Secure Code - Day07 -Presentation Buffer OverflowsПодробнее

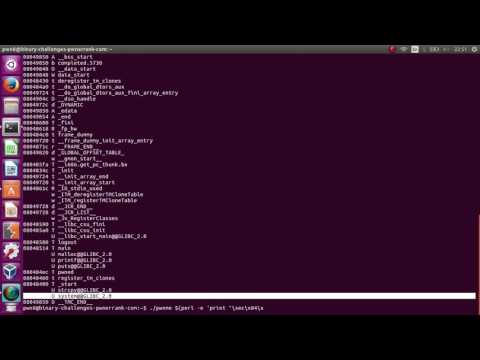
Exploit-Exercises Protostar Stack3 ExploitПодробнее

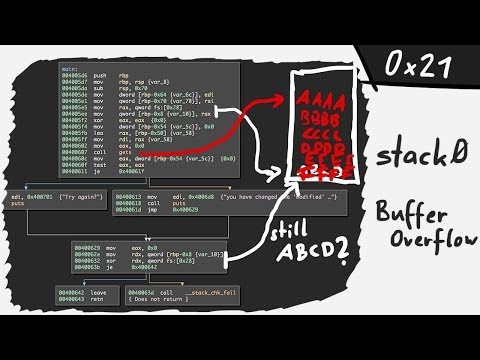
Buffer overflow on a modern system impossible? stack0: part 1 - bin 0x21Подробнее