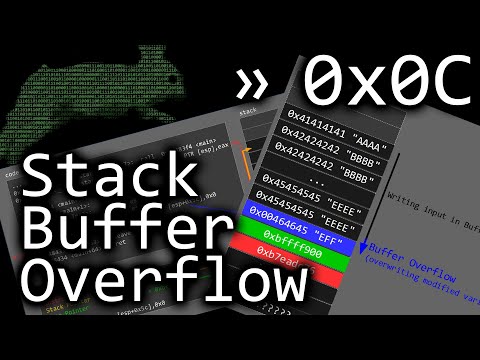
First Stack Buffer Overflow to modify Variable - bin 0x0C
Protostar stack1 - Buffer overflow to change variableПодробнее
Stack Buffer Overflow to Modify Variable in Protected Memory| Protostar 101|Binary Exploit TutorialПодробнее
Buffer Overflow to Modify Variable Values - pwn102 - PWN101 | TryHackMeПодробнее
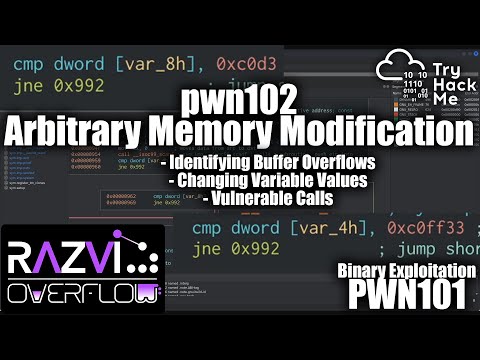
Bin 0x1 | C and a simple buffer overflowПодробнее

Protostar stack2 - Enviroment variables and buffer overflowsПодробнее
Binary Exploitation, Stack based Buffer Overflow - Local variablesПодробнее
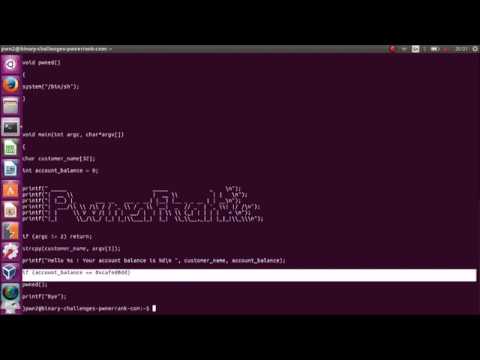
How to find offset by using cyclic in stack based buffer overflow exploitПодробнее
#1 Introduction to stack buffer overflow attack - Protostar Stack0 - binary exploitation شرح بالعربيПодробнее

First Exploit! Buffer Overflow with Shellcode - bin 0x0EПодробнее
Buffer OverflowПодробнее

#2 understanding stack buffer overflow - Protostar Stack1 - binary exploitation شرح بالعربيПодробнее
Buffer Overflow - 13 Defense Against Buffer OverflowsПодробнее

Protostar stack0 - First buffer overlfow to change variable valueПодробнее
BDSec CTF 2023 | PWN writeup | Buffer Overflow | Overwrite variable and Call functionПодробнее