How to exploit a buffer overflow vulnerability - Practical
How to Exploit a Buffer Overflow to Bypass Username Validation in C CodeПодробнее

How to Exploit Vulnerabilities with Buffer Overflow TechniquesПодробнее
Hacker Course Buffer Overflow A Practical Example with ExploitПодробнее
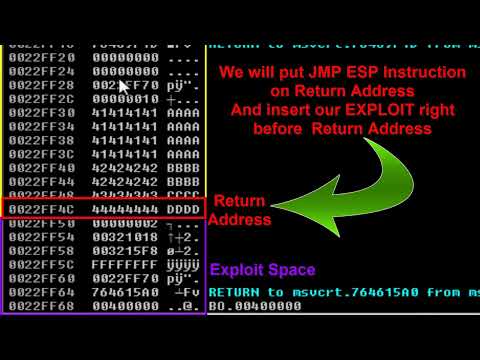
Sudo Buffer Overflow | Tryhackme Lab | Cyber securityПодробнее
Buffer Overflow | tryhackme | Practical | Part-04 | CrifoxulПодробнее

Buffer Overflow | tryhackme | Practical | Part-03 | CrifoxulПодробнее

Mastering Buffer Overflow: Coffee V1 CTF Penetration Testing WalkthroughПодробнее
Buffer Overflow | tryhackme | Practical | Part-02 | CrifoxulПодробнее

Buffer Overflow | tryhackme | Practical | Part-01 | CrifoxulПодробнее

Buffer OverflowПодробнее

Buffer Overflow Explained With PracticalПодробнее

Linux Buffer Overflow - Exploit Development 9Подробнее

What is Buffer Overflow Attack and Practical in #hindi #englishПодробнее
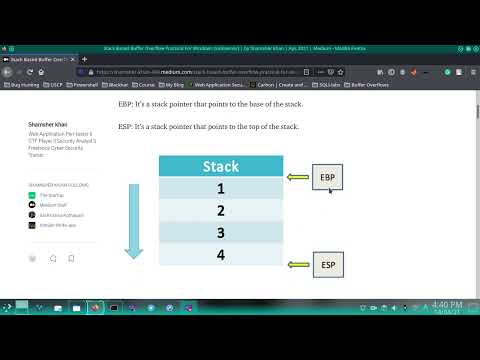
Buffer Overflow - SPIKING!Подробнее
Return to LibC Attack Bypass NX, PIE: Stack Buffer OverflowПодробнее
Buffer Overflows: A Symphony of ExploitationПодробнее
buffer overflow 0- picoCTF practice challenges { Binary Exploitation }Подробнее
buffer overflow 1- picoCTF practice challenges { Binary Exploitation }Подробнее
clutter overflow - picoCTF practice challenges { Binary Exploitation }Подробнее

why do hackers love strings?Подробнее
