Buffer overflow on a modern system impossible? stack0: part 1 - bin 0x21
Running a Buffer Overflow Attack - ComputerphileПодробнее
Vulnhub - Buffer OverFlow : SmashTheTux Level 0x00Подробнее

Stack Smashing Protection - Part 1 - DisassemblyПодробнее
Windows 10 Enterprise Buffer OverFlow | CTF WalkthroughПодробнее
How to Exploit a Simple Buffer Overflow Vulnerability (ARM64 iOS)Подробнее

04. Stack Smashing & User Input Preparation | Buffer Overflow Attack [Bangla]Подробнее
![04. Stack Smashing & User Input Preparation | Buffer Overflow Attack [Bangla]](https://img.youtube.com/vi/0TM642K-TYY/0.jpg)
Buffer overflow example (vulnserver.exe and TRUN command)Подробнее
First Stack Buffer Overflow to modify Variable - bin 0x0CПодробнее
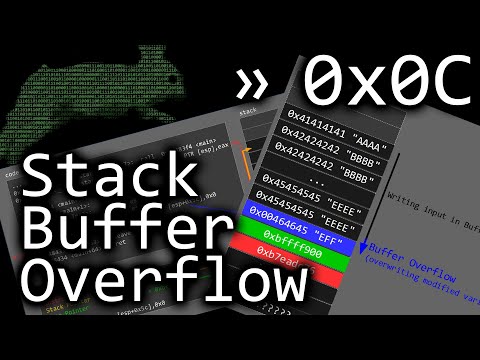
Buffer Overflow (Stack) Exploitation Demo (Windows XP 32-bit SP2) Part 1Подробнее
Buffer Over Flow Explained and Simplified P6 - TheoryПодробнее
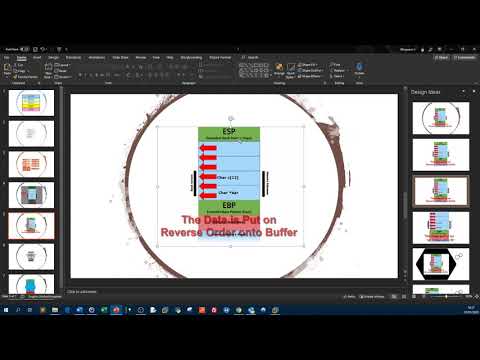
iamismael - Buffer Overflow Tutorial 1/2: IntroПодробнее

Protostar stack1 - Buffer overflow to change variableПодробнее