Stack Buffer Overflow to Modify Variable in Protected Memory| Protostar 101|Binary Exploit Tutorial
Protostar stack1 - Buffer overflow to change variableПодробнее
First Stack Buffer Overflow to modify Variable - bin 0x0CПодробнее
How to Protect Stack Buffer Overflow and Bypass TechniquesПодробнее

Buffer Overflow to Modify Variable Values - pwn102 - PWN101 | TryHackMeПодробнее
How to exploit a buffer overflow vulnerability - PracticalПодробнее
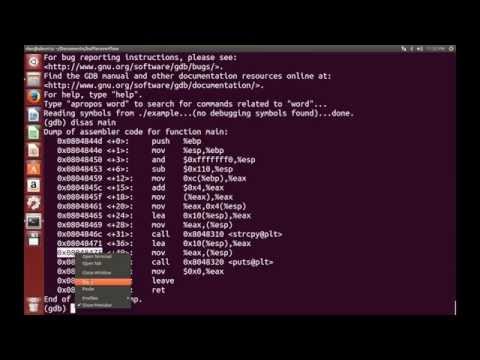
How to exploit buffer overflow - protostar challenge 5Подробнее
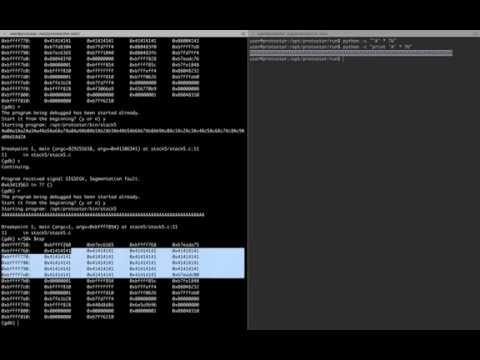
Binary Exploitation, Stack based Buffer Overflow - Local variablesПодробнее
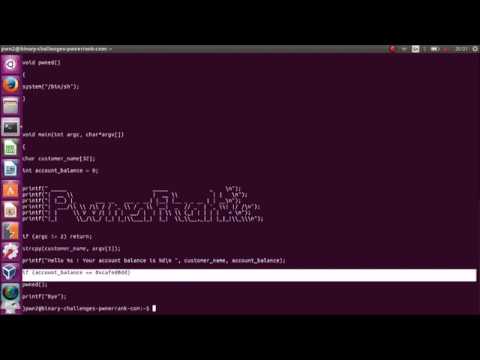
How to find offset by using cyclic in stack based buffer overflow exploitПодробнее
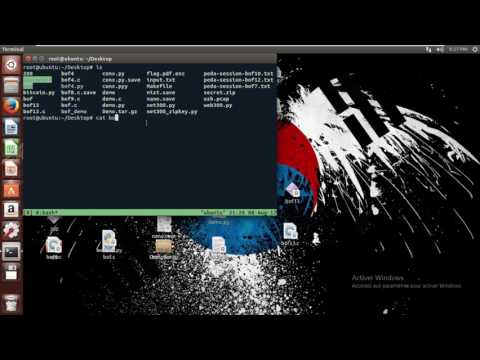
Buffer Overflow ExploitПодробнее
Exploiting Buffer Overflow (BOF) tutorial - pwn101 - PWN101 | TryHackMeПодробнее
Stack Buffer Overflow exampleПодробнее

#1 Introduction to stack buffer overflow attack - Protostar Stack0 - binary exploitation شرح بالعربيПодробнее

#2 understanding stack buffer overflow - Protostar Stack1 - binary exploitation شرح بالعربيПодробнее
Understanding Buffer Overflow Attacks to Exploit Variables in C ProgrammingПодробнее
L11 03 Stack Overflow Corrupts MemoryПодробнее

Binary Exploitation vs. Web SecurityПодробнее
