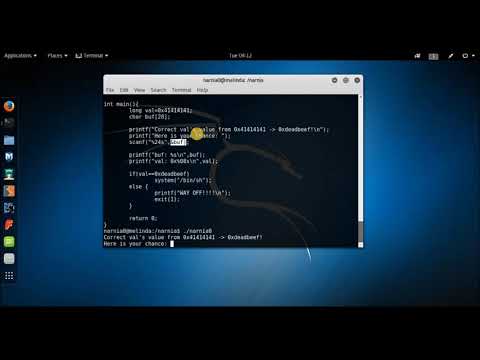
Persistent backdoor after buffer overflow attack getting inside of Windows 10

Live Buffer Overflow Attack From Windows 10 System | Basic Stack Overflow Explained Complete 10 MinПодробнее
Windows 10 Enterprise Buffer OverFlow | CTF WalkthroughПодробнее
Running a persistent Backdoor on hacked computerПодробнее

Buffer OverflowПодробнее

Another buffer overflow through command line argument on Windows 10Подробнее

Exploit Windows XPSP3 and Persistence BackdoorПодробнее

Hacking Windows 10 using Buffer Overflow.Подробнее

HACKED! How a Buffer Overflow Exploit works, plus Code Red!Подробнее
stack buffer overflow exploit to run calculator on windows 11Подробнее
What to learn after buffer overflows #exploit #cybersecurity #hacking #programming #learn #techПодробнее

how do hackers exploit buffers that are too small?Подробнее

Windows Buffer Overflow IntroductionПодробнее

Buffer Overflow Hacking Tutorial (Bypass Passwords)Подробнее
Running a Buffer Overflow Attack - ComputerphileПодробнее
Buffer Overflow Attack to Domain Admin vs Security Onion | Attack and DetectПодробнее
How to exploit a buffer overflow vulnerability - PracticalПодробнее
Buffer OverflowПодробнее

Creating Backdoor For Windows -10 in Empire[part-2] |Basic windows 10 hacking workflow| PANTHER TECHПодробнее
![Creating Backdoor For Windows -10 in Empire[part-2] |Basic windows 10 hacking workflow| PANTHER TECH](https://img.youtube.com/vi/msHSN_CJYWk/0.jpg)
024 Binary Exploitation Buffer overflow attackПодробнее