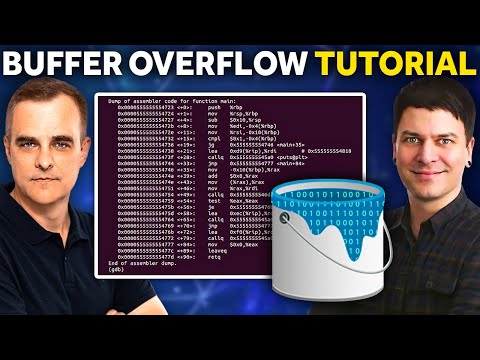
What to learn after buffer overflows #exploit #cybersecurity #hacking #programming #learn #tech

Learn Buffer Overflow Hacking From Zero to Hero!Подробнее

System Hacking : Buffer Overflow , Privilege Escalation & Maintaining Access Made EasyПодробнее
Understanding Buffer Overflow: A Key Cybersecurity Vulnerability | Explained Under 60 SecondsПодробнее

6 Types of Exploit Every Hacker Should Know! | #cybersecurity #ethicalhacking #tech #hackersПодробнее

How to Exploit Vulnerabilities with Buffer Overflow TechniquesПодробнее
Buffer Overflow Explained: How Hackers Exploit It and How to Protect Yourself!Подробнее

Buffer Overflow Exploit: A Step-by-Step Tutorial for BeginnersПодробнее
Live Hacking #6: Introduction To Binary Exploitation (PART I)Подробнее
Mastering Buffer Overflow : Identify and Exploit Applications with Buffer/Stack OverflowПодробнее

A Brief Overview of Stack-Based Buffer Overflow | Cyber Security Webinar | CWLabsПодробнее

Mastering Metasploit with OTW: A Linux Ethical Hacking TutorialПодробнее

Developing a Buffer Overflow Exploit - Cybersecurity Class Final ProjectПодробнее

Hacking Demystified: Unveiling a Real-World Buffer Overflow Exploit #ethicalhacking #cybersecurityПодробнее

Learn Binary Exploitation with PicoCTF's Stonke Challenge: A Beginner's GuideПодробнее

[HINDI] What's a Buffer Overflow? (And Why You Should Care!) - Lab IncludedПодробнее
![[HINDI] What's a Buffer Overflow? (And Why You Should Care!) - Lab Included](https://img.youtube.com/vi/zcOOv501UHE/0.jpg)
Linux Buffer Overflow - Exploit Development 9Подробнее

How do hackers exploit buffers that are too small || What happens after a buffer overflowsПодробнее

What is a Stack Buffer Overflow? Exploring How To Exploit the StackПодробнее
Buffer Overflow Hacking Tutorial (Bypass Passwords)Подробнее