Exploit Development Part 2 : Finding and Overwriting Offset

Exploit Development Part 2 Finding and Overwriting OffsetПодробнее

#HITB2021AMS D1T1 - Bypassing DEP With Jump-Oriented Programming - B. Brizendine and A. BabcockПодробнее

Mainframe [z/OS] Reverse Engineering and Exploit DevelopmentПодробнее
![Mainframe [z/OS] Reverse Engineering and Exploit Development](https://img.youtube.com/vi/3K80dWbQsqE/0.jpg)
OverWriting Variable Value - Part IIПодробнее

Exploit Development: Looking Unknown Vulnerabilities | Stack Buffer Overflow LAB Part 2Подробнее
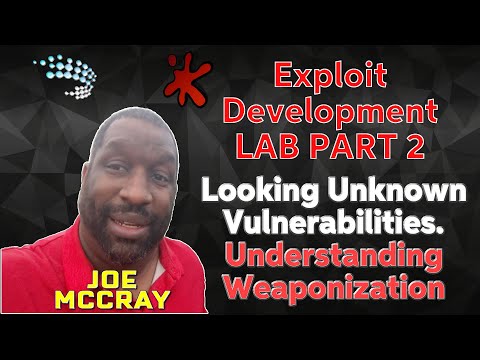
Exploit Development I - Basics: SEH overwriteПодробнее

Exploit Development | Format Strings Series 6/6 - x64 exploitation + Final thoughtsПодробнее

Writing Exploits (Buffer Overflows Part 2)Подробнее
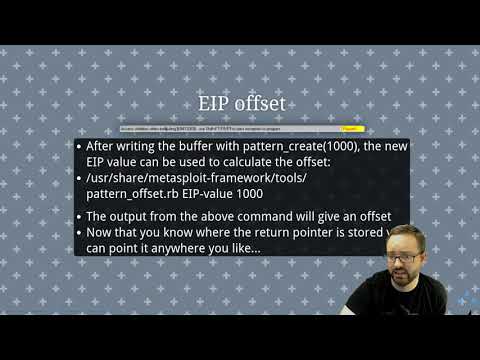
Video 2 - Basic Exploit Development - Direct Buffer OverflowПодробнее

Bug Hunting and Exploit Development 4: Writing Metasploit Framework MSF Exploit ModulesПодробнее

OverWriting Variable Value - Part IПодробнее

Module 2.2 (Fuzzing): Using SEH Overwrite to exploit Windows softwareПодробнее

Binary Exploit Development - SEH Based OverflowПодробнее
Exploit Development: Looking Unknown Vulnerabilities | Stack Buffer Overflow LAB (Part 1). 2021Подробнее

Binary Exploit Development Tutorial - Simple Buffer OverflowПодробнее
Module 2.5 (Bad character analysis): Using SEH Overwrite to exploit Windows softwareПодробнее

Structured Exception Handler Overwrite Part 1Подробнее
Bug Hunting and Exploit Development 3: Finding Flaws Using Fuzzing 2Подробнее
