Writing Exploits (Buffer Overflows Part 2)
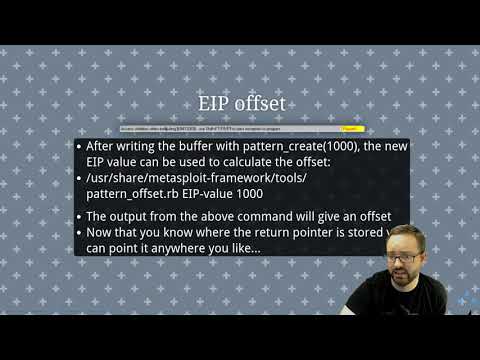
Dns remote code execution writing the exploit part 2Подробнее

Firmware 3: Buffer Overflow Part 2 (Hijack The Execution)Подробнее

Part-2 - Anatomy of a Python Scripted Remote Buffer Overflow w/ Joff ThyerПодробнее

Part-1 - Anatomy of a Python Scripted Remote Buffer Overflow w/ Joff ThyerПодробнее

Overwriting RBP with an Off-by-One Buffer Overflow - Cake - [Intigriti 1337UP LIVE CTF 2022]Подробнее
![Overwriting RBP with an Off-by-One Buffer Overflow - Cake - [Intigriti 1337UP LIVE CTF 2022]](https://img.youtube.com/vi/jU7yB-elFV8/0.jpg)
2: Overwriting Variables on the Stack (pt 2) - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее

Lab07 SEED 2.0 Buffer-Overflow Attack Lab (Server Version) Part IIПодробнее

How to Exploit a Buffer Overflow VulnerabilityПодробнее

Ep2 Part 1: "Writing Buffer Overflow Exploit” & How To Use It On A Real Life x86 MachineПодробнее

Ep2 Part 2: "Writing Buffer Overflow Exploit” & How To Use It On A Real Life x86 MachineПодробнее

Lecture 3 - Stack smashing attacks, malware, Buffer overflows - Part 2Подробнее

Lecture 2 - Stack smashing attacks, malware, Buffer overflows - Part 1Подробнее
[HINDI] Introduction to Buffer Overflows | Writing an Exploit | Part #3 : Generating ShellcodeПодробнее
![[HINDI] Introduction to Buffer Overflows | Writing an Exploit | Part #3 : Generating Shellcode](https://img.youtube.com/vi/ulKU9X4RIXY/0.jpg)
[HINDI] Introduction to Buffer Overflows | Writing an Exploit | Part #2 : Finding Bad CharactersПодробнее
![[HINDI] Introduction to Buffer Overflows | Writing an Exploit | Part #2 : Finding Bad Characters](https://img.youtube.com/vi/Sp9lqwQx9CQ/0.jpg)
[HINDI] Introduction to Buffer Overflows | Writing an Exploit | Part #1 : FuzzingПодробнее
![[HINDI] Introduction to Buffer Overflows | Writing an Exploit | Part #1 : Fuzzing](https://img.youtube.com/vi/ZYSfsHk6esE/0.jpg)
[HINDI] Introduction to Buffer Overflows | Simple C ProgramПодробнее
![[HINDI] Introduction to Buffer Overflows | Simple C Program](https://img.youtube.com/vi/4QTNt0RS2Sc/0.jpg)
Exploit Development: Looking Unknown Vulnerabilities | Stack Buffer Overflow LAB Part 2Подробнее
Exploit Development: Looking Unknown Vulnerabilities | Stack Buffer Overflow LAB (Part 1). 2021Подробнее

Buffer overflow on Stack | Memory Overwrite | RIP alteration | A visual comprehensive explanation.Подробнее
