iamismael - Buffer Overflow Tutorial 1/2: Intro

iamismael - Buffer Overflow 2/2: Vuln Server WalkthroughПодробнее

Buffer Overflow Tutorial - Part 1Подробнее

BufferOverflow with kali linux and vulnserver 1/2Подробнее
(S) Buffer Overflow - Learning Hacking @ TryHackMe 1/2 (2024-08-07)Подробнее

Intro to Buffer Overflows - Part 1Подробнее
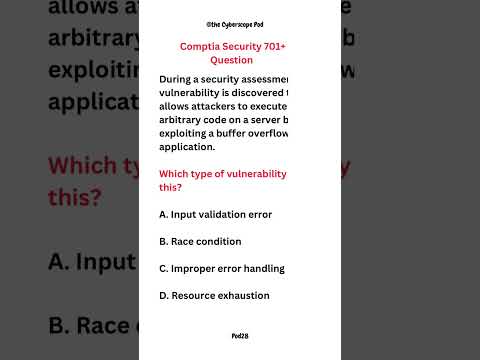
CompTIA Security+ (SY0-701) Question: Buffer Overflow VulnerabilityПодробнее
Demonstrationg Buffer Overflow and ASLR Protection P4 | CTF WalkthroughПодробнее

FreeType: FreeType buffer overflow (CVE-2025-27363) #shortsПодробнее

Buffer Overflow (Stack) Exploitation Demo (Windows XP 32-bit SP2) Part 1Подробнее
Intro to Buffer Overflow and Binary Exploitation (PicoGym)Подробнее

(S) What's missing from my Buffer Overflow strategy? (2025-01-17) 1/2Подробнее

#4 BrainPan 1 (Try Hack Me) (Hard) (Buffer Overflow)Подробнее

Buffer Overflow in networking applications P10 | TryHackMe Intro To PwntoolsПодробнее
Buffer Overflow & Binary Exploitation with Radare2 | P21 | CTF WalkthroughПодробнее
What’s a Buffer Overflow 🤔🤔 #coding #appdevelopmentПодробнее

🧠 Think you know your backdoor from your buffer overflow?Подробнее

Ransomware Attacks: Predicting Vulnerabilities & TrendsПодробнее

Buffer OverflowПодробнее

Bufferoverflow part 2- machine shellcoding 1/2Подробнее
