WordPress Penetration Testing & Security Course | C:06 | Hardening & Configurations | PentestHint
WordPress Penetration Testing & Security Course | C:06 | Hardening & Configurations | PentestHintПодробнее

WordPress Penetration Testing & Security Course | C:05 | Recon | Pre & Post ExploitationПодробнее

WordPress Penetration Testing & Security Course | C:04 | WordPress Setup Manually | PentestHintПодробнее

WordPress Penetration Testing & Security Course | C:02 | WordPress Security Fundamentals PentestHintПодробнее

WordPress Penetration Testing & Security Course | C:07 | Advance Wordpress Security | PentestHintПодробнее

WordPress Penetration Testing & Security Course | C:01 | Introduction | PentestHintПодробнее

Roadmap to Penetration Tester | EP:12 | Web Application Pentesting | WORDPRESS PENETRATION TESTINGПодробнее

How to Begin Your Penetration Testing Career | Skills, Certs & AdviceПодробнее

How to Test Wordpress with WPForce - [Penetration Testing]Подробнее
![How to Test Wordpress with WPForce - [Penetration Testing]](https://img.youtube.com/vi/CYTJOLRYCtk/0.jpg)
A Day in the Life of Cyber Security | SOC Analyst | Penetration Tester | Cyber Security TrainingПодробнее

Why Kali Linux Is Used For Hacking ? | Kali Linux For Ethical Hackers #Shorts #SimplilearnПодробнее

SQL Injection 101: Exploiting VulnerabilitiesПодробнее

Becoming a Security Research EngineerПодробнее

Hacking KnowledgeПодробнее

Simple Penetration Testing Tutorial for Beginners!Подробнее

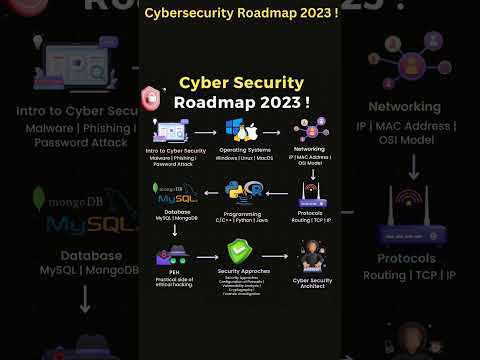
Cybersecurity Roadmap 2023 ! #cybersecurityПодробнее
Here's a quick look at a path to becoming a webapp pentester! #webapp #pentesting #cybersecurityПодробнее

CyberSecurity Definitions | Penetration TestingПодробнее

How to insure the Security / Penetration Testing for Mobiles apps and websitesПодробнее
