Windows Exploit Development Remote Stack Buffer Overflow
Exploit Development: Writing a Remote Buffer Overflow Exploit for Windows 11 RCEПодробнее

Remote Buffer OverFlow P22 and Windows Privilege Escalation | CTF WalkthroughПодробнее

Exploit Development: MP3 Player (Windows Stack Based)Подробнее

VulnServer Stack Buffer Overflow Exploit Development on Windows 7Подробнее
Module 2.6 (Cracking the shell): Using SEH Overwrite to exploit Windows softwareПодробнее

Module 2.5 (Bad character analysis): Using SEH Overwrite to exploit Windows softwareПодробнее

Module 2.3 (PoC creation): Using SEH Overwrite to exploit Windows softwareПодробнее

Module 1.6 (Cracking the shell): Creating a stack-based buffer overflow Windows exploitПодробнее

Module 1.5 (Bad character analysis): Creating a stack-based buffer overflow Windows exploitПодробнее

Module 1.4 (Controlling the execution): Creating a stack-based buffer overflow Windows exploitПодробнее

Module 1.3 (PoC Creation): Creating a stack-based buffer overflow Windows exploitПодробнее

Module 1.2 (Fuzzing): Creating a stack-based buffer overflow Windows exploitПодробнее

Module 1.1 (Introduction): Creating a stack-based buffer overflow Windows exploitПодробнее

DEF CON 26 - Josep Pi Rodriguez - WingOS: How to Own Millions of Devices .Подробнее

SLmail Buffer Overflow Exploit Development with Kali LinuxПодробнее
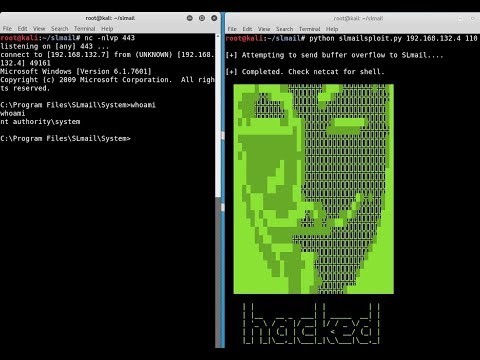
$Hell on Earth: From Browser to System CompromiseПодробнее

Hack Remote Windows PC with Watermark master buffer overflow exploit Kali LinuxПодробнее
Video 2 - Basic Exploit Development - Direct Buffer OverflowПодробнее

Buffer Overflow Exploit Development - Part 02Подробнее
Exploit DevelopmentПодробнее
