Exploit Development: Writing a Remote Buffer Overflow Exploit for Windows 11 RCE

Sync Breeze 10.0.28 Proof of Concept | Vanilla Stack Buffer Overflow | Exploit DevelopmentПодробнее
stack buffer overflow exploit to run calculator on windows 11Подробнее
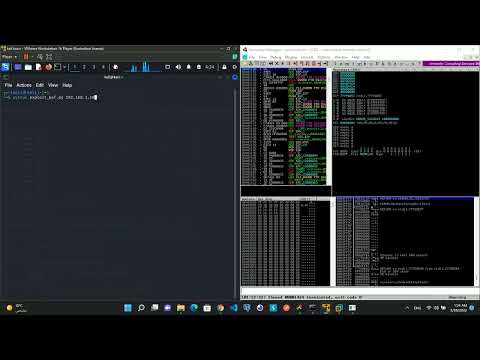
Windows Exploit Development Remote Stack Buffer OverflowПодробнее

Smashing TRUN Command with Vanilla Stack Exploitation | VULNSERVER | Windows EXP-DEV 0x1Подробнее
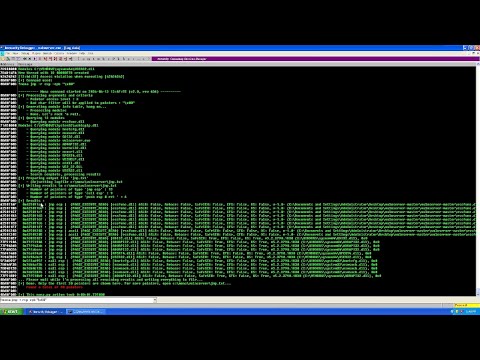
Remote Windows Buffer Overflow | ExploitDevПодробнее
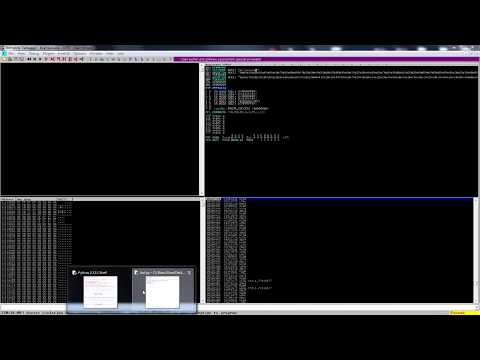
Basics of buffer overflow - Deep dive into exploit writing (exploit development)Подробнее
Exploit Writing 1: Stack Based Overflows (corelan.be)Подробнее
Buffer overflow bypass dep using ropПодробнее

ED 201: Linux Buffer Overflow With Command InjectionПодробнее
Video 2 - Basic Exploit Development - Direct Buffer OverflowПодробнее

Free Float FTP Server Buffer Overflow Vulnerable | Exploit Development with PythonПодробнее
Module 1.1 (Introduction): Creating a stack-based buffer overflow Windows exploitПодробнее

Python for exploit development All about buffer overflowsПодробнее

Module 2.4 (Controlling the execution): Using SEH Overwrite to exploit Windows softwareПодробнее

VulnServer Stack Buffer Overflow Exploit Development on Windows 7Подробнее
Binary Exploitation Buffer Overflow Explained in DetailПодробнее

CloudMe Sync Remote Buffer Overflow - CVE-2018-6892Подробнее

Learning Metasploit : Exploit Development Concepts | packtpub.comПодробнее
