Buffer Overflow Explained: How Hackers Exploit It and How to Protect Yourself!

Buffer Overflow Attacks Explained | How Hackers Exploit Memory?Подробнее

IPv6 keeps getting hacked on WindowsПодробнее

Атака переполнения буфера, объясненная в кибербезопасностиПодробнее
Buffer Overflow Suffi Buffer Overflow Su How To Protect Yourself From Unethical HackingПодробнее

How To Protect Yourself from Buffer Overflow Attacks?Подробнее

how do hackers exploit buffers that are too small?Подробнее

why do hackers love strings?Подробнее

Giving Hackers a Headache with Exploit Mitigations - Maria Markstedter, Azeria LabsПодробнее

DEF CON Safe Mode - Shlomi Oberman, Moshe Kol, Ariel Schön - Hacking the Supply ChainПодробнее

How to Hack a Turned-Off Computer, or Running Unsigned Code in Intel Management EngineПодробнее

Buffer Overflow Explanation In Hindi 🔥🔥Подробнее

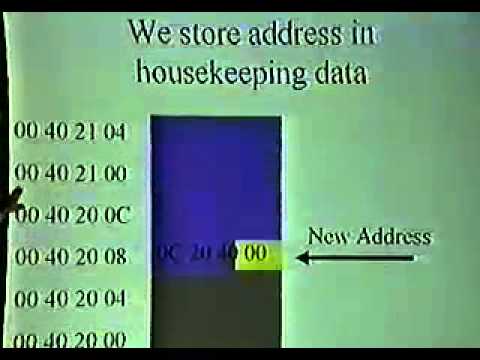
DEF CON 8 - Greg Hoglund - Advanced Buffer Overflow TechniquesПодробнее