Système d'exploitation💻 |operating system💻|sistema de explotación🖥
SYSTÈME D'EXPLOITATION 32 OU 64 BITS !!!!!! #laptop #operatingsystemПодробнее

Système d'exploitation💻 |operating system💻|sistema de explotación🖥Подробнее

METASPLOIT - EXPLOITING ANDROIDПодробнее

Kernel Root Exploit via a ptrace() and execve() Race ConditionПодробнее

Immunity Canvas & Exploit PacksПодробнее

Windows 10 Kernel Mitigations and Exploitation w/ Jaime Geiger & Stephen Sims - SANS HackFest SummitПодробнее

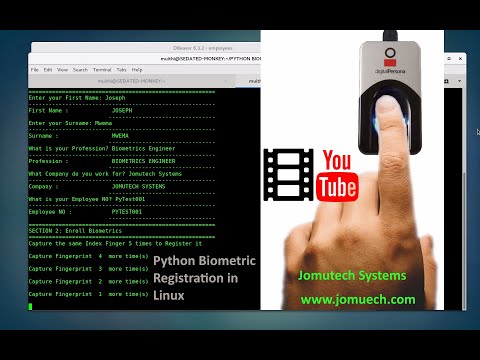
Python Biometric Registration and Authentication on Linux using DigitalPersona 4500 and MariaDB SQLПодробнее
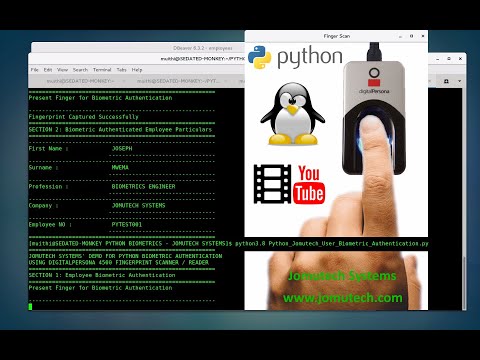
Python Biometric Registration in Linux and Saving of Enrolled Biometric Fingerprint Data in MariaDBПодробнее
Exploitation of a Modern Smartphone BasebandПодробнее

DEF CON 26 CAR HACKING VILLAGE - Nathaniel Boggs - Automotive Exploitation SandboxПодробнее

Vlog #011: Operating Systems - books & resourcesПодробнее

Subverting Apple Graphics: Practical Approaches to Remotely Gaining RootПодробнее

$Hell on Earth: From Browser to System CompromiseПодробнее

Vulnerability Exploitation In Docker Container EnvironmentsПодробнее

Exploiting Adobe Flash Player In The Era Of Control Flow GuardПодробнее

Parallel computing and the OSПодробнее

Heap Models for Exploit SystemsПодробнее

Information Gathering: Computer Security Lectures 2014/15 S1Подробнее

Practical Exploitation of Embedded SystemsПодробнее

Black Hat USA 2013 - Hacking like in the Movies: Visualizing Page Tables for Local ExploitationПодробнее
