SHA 512 Algorithm Part 1
4.6.1 SHA 512 Algorithm Part -1Подробнее

4.9.3 Secure Hash Algorithm Part 3 in TamilПодробнее

4.9.1 Secure Hash Algorithm Part 1 in TamilПодробнее

SHA-512 in PythonПодробнее

🔐 What is SHA-512? 🔐 (Part 1/2) | Background and things you need to know to understand SHA-512Подробнее

🔐 What is SHA-512? 🔐 (Part 2/2) | The step-by-step explanation of the algorithm ➕ A detailed exampleПодробнее

SHA - 512 Algorithm in Hindi || information security & cyber security || Study easier by Pooja PatelПодробнее

SHA-1 (Secure Hash Algorithm - 1) Part-2 Working Explained in HindiПодробнее

SHA-1 (Secure Hash Algorithm - 1) Part-1 Working Explained in HindiПодробнее

Lec-30_SHA-512 Part-1|Information Security | Computer EngineeringПодробнее

SHA - 512 | secured hash algorithm explained in Gujarati (notes) #informationsecurityinonemimuteПодробнее

SHA -512 I secured hash algorithm explained in GujaratiПодробнее

Network security - Secure Hash Algorithm Part-2(SHA-512Подробнее

SHA 512 - Secure Hash Algorithm - Step by Step Explanation - Cryptography - Cyber Security - CSE4003Подробнее
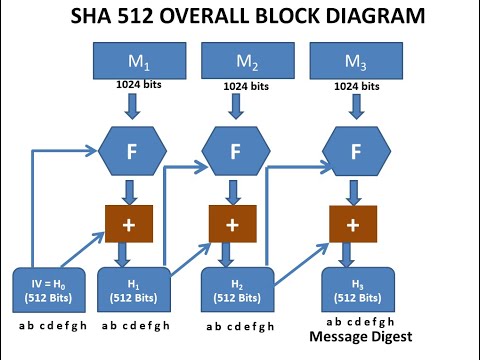
Secure Hash Algorithm SHA512 Lect2 by Dr. I. B. Lal (Cryptography & Network Security)Подробнее

SHA 1 | Secure Hash Algorithm | Working of SHA 1 | Parameters of SHA512 and SHA 256Подробнее

Lab 3.3 Setting up Authentication SHA 512 in OSPF part 1Подробнее

Secure Hash Algorithm SHA-1 SHA-512 Cryptography & Network Security | Information System SecurityПодробнее

Learning Veracrypt Part 15, What is SHA-512?Подробнее

SHA 512 Algorithm Part 3Подробнее
