Network security - Secure Hash Algorithm Part-2(SHA-512

Secure Hash Algorithm-SHA-512-KTU CST 433 Security in Computing S7 CS- Mod 4 Part 11Подробнее

4.9.3 Secure Hash Algorithm Part 3 in TamilПодробнее

4.9.2 Secure Hash Algorithm Part 2 in TamilПодробнее

4.9.1 Secure Hash Algorithm Part 1 in TamilПодробнее

Hash Functions & Digital Signatures | Chapter-5 | Cryptography & Network Security | nesoacademy.orgПодробнее

🔐 What is SHA-512? 🔐 (Part 1/2) | Background and things you need to know to understand SHA-512Подробнее

🔐 What is SHA-512? 🔐 (Part 2/2) | The step-by-step explanation of the algorithm ➕ A detailed exampleПодробнее

SHA-1 (Secure Hash Algorithm - 1) Part-2 Working Explained in HindiПодробнее

SHA-1 (Secure Hash Algorithm - 1) Part-1 Working Explained in HindiПодробнее

Network Security - Secure Hash Algorithm (Part-I)Подробнее

SHA 512 - Secure Hash Algorithm - Step by Step Explanation - Cryptography - Cyber Security - CSE4003Подробнее
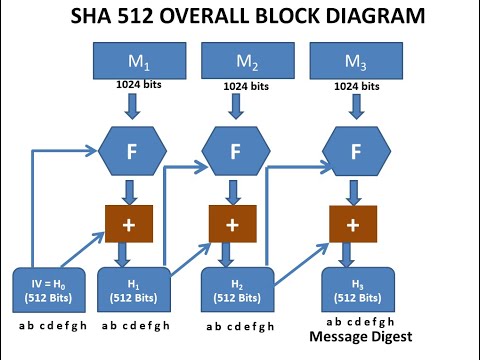
Secure Hash Algorithm SHA512 Lect2 by Dr. I. B. Lal (Cryptography & Network Security)Подробнее

SHA 1 | Secure Hash Algorithm | Working of SHA 1 | Parameters of SHA512 and SHA 256Подробнее

Network security lecture No. 13 By: Ms Sadaf AsadПодробнее

Secure Hash Algorithm SHA-1 SHA-512 Cryptography & Network Security | Information System SecurityПодробнее

Learning Veracrypt Part 15, What is SHA-512?Подробнее

SHA 512 Algorithm Part 3Подробнее

SHA 512 Algorithm Part 2Подробнее

SHA 512 Algorithm Part 1Подробнее
