SHA-256 & SHA-512 Explained 🔥 | Secure Hashing Algorithm Tutorial
How To Find The Hash Of A File? - Tactical Warfare ExpertsПодробнее

How To Password Cracking EXPLAINED: SHA256, SHA512, MD5 | Hash Attacks & Tools!Подробнее

What Is A Hash Function How SHA256 Works In Blockchain Cryptography Used Hashing Algorithm ExplainedПодробнее

SHA-256 & SHA-512 Explained 🔥 | Secure Hashing Algorithm TutorialПодробнее

Secure Hash Algorithm (SHA) in Cryptography and Network Security #cryptography #networking #securityПодробнее
16-Golang-Session Mastering Golang: Rune, Big Int, and SHA Explained! 🚀 (By Jiten Palaparthi)Подробнее

** Master Hashing: MD5 ,Blake2 to SHA512!**Подробнее

SHA Algorithm Explained | Unit 4 Cryptography and Cyber Security (CB3491) | Anna UniversityПодробнее

Length Field and Padding in SHA 512 || Lesson 75 || Cryptography || Learning Monkey ||Подробнее

Understanding MD5, SHA256, and SHA512 Hashing AlgorithmsПодробнее

Hash function selection in blockchain | IIS PresentationПодробнее

SHA 512 || Secure Hash Algorithm || Cryptographic Hash function || asymmetric cryptograpyПодробнее

[Hindi] What is Hashing with Example | Hashing Algorithm | MD5 | SHA256Подробнее
![[Hindi] What is Hashing with Example | Hashing Algorithm | MD5 | SHA256](https://img.youtube.com/vi/tzB5VD-DzJE/0.jpg)
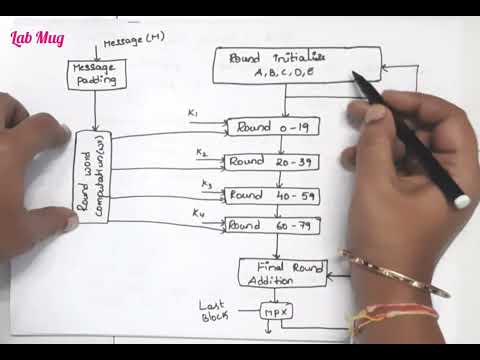
SECURE HASH ALGORITHM – SHA 512Подробнее

4.9.1 Secure Hash Algorithm Part 1 in TamilПодробнее

Understanding SHA-256 Algorithm @FAMEWORLDEDUCATIONALHUBПодробнее

#25 - Different Forms Of SHA | Blockchain Tutorial @FameworldeducationalhubПодробнее

VERIFY MD5 / SHA256 Hash or Checksum on Linux - File Security (Ubuntu)Подробнее
SHA256 Hash Generator Online Tool | bulkwebtools.ioПодробнее

char gpt roblox studio HASH SHA-256 -SHA-512-MD5Подробнее
