Phishing & SQL Injection: Cyber Attacks Explained in Seconds!
Phishing & SQL Injection: Cyber Attacks Explained in Seconds!Подробнее

Cyber Threats Explained in 60 Seconds | 8 Most Common Cybersecurity Threats in 2025 #cybersecurityПодробнее

h@cktivitycon 2020: You've got pwned: exploiting e-mail systemsПодробнее

What are SQL Injections? // Explained in 180 secondsПодробнее

Phishing AttackПодробнее

What Is SQL Injection?Подробнее
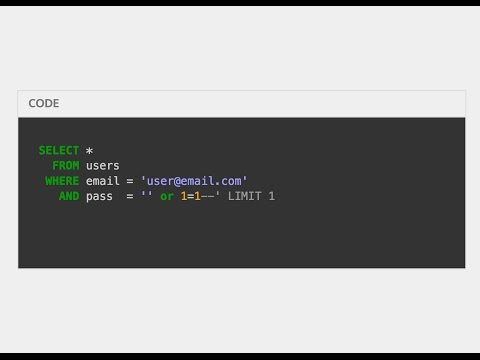
Top 5 Types of Cyber Attacks Explained | the21stCen | #CyberAttack #Phishing #DDoS #SQLInjectionПодробнее

SQL Injections are scary!! (hacking tutorial for beginners)Подробнее

Top Cyber attacks Explained 2025Подробнее

Phishing Explained In 6 Minutes | What Is A Phishing Attack? | Phishing Attack | SimplilearnПодробнее

Practical Demo of SQL Injection #viral #cybersecurityПодробнее
SQL Injection Attacks - Explained in 5 MinutesПодробнее

Every Type of Cyber Attack Explained in 8 MinutesПодробнее

Database Breached: The Power of SQL InjectionПодробнее
SQL Injection | Hack the Box | FacultyПодробнее
SQL Injection Explained | SQL Injection Attack in Cyber Security | Cybersecurity | SimplilearnПодробнее
SQL Injection Attack | DemoПодробнее

Cyber Security Interview Questions and Answers | Data Leakage, Phishing, SQL Injection, and DNSПодробнее

Running an SQL Injection Attack - ComputerphileПодробнее
What is Cyber Attack? Top 10 Types of Cyber Attacks Explained 2025Подробнее

SQL Injection - CompTIA Security+ SY0-701 - 2.3Подробнее

Find SQL Injection vulnerability with sqlmapПодробнее