NETWORK SECURITY - RSA ALGORITHM part 2
Security Sessions - Armadillo X RSA - Part 2Подробнее

Wireshark 101 THM Part 2 (http & https) Decrypt with RSA keyПодробнее

#25 RSA Encryption | Part 2 | Quantum Algorithms & CryptographyПодробнее

Can quantum computers break encryption? Part 2 #encryption #quantum #quantumcomputingПодробнее

Rap MonstermПодробнее

Information Technology Act 2000 Part 2 | Chapter IПодробнее

Rsa Explained: Understanding Asymmetric/public Key Encryption | Https Series Part 2/4 🧐Подробнее

What is a Bitcoin? Decentralized Network. Cryptography ( Part2 ).Подробнее

4.9.2 Secure Hash Algorithm Part 2 in TamilПодробнее

1.7.5 Playfair Cipher Part 2 in TamilПодробнее

wolfSSL Training Part 2Подробнее

Breaking Analysis: RSA 2023 Security Identity Crisis Part 2Подробнее

Security, Symmetric & Asymmetric Algorithm, RSA Algorithm (Part-2)Подробнее

Cyber Security Interview Questions and Answers - Part 2 | Invensis LearningПодробнее

Understanding RSA Algorithm - Part 2 (Urdu / Hindi)Подробнее

Lec 5|| Perfect Secrecy Part II#fahadusman#cryptographyПодробнее

Suzanne RSA lecture 2022-04-26 part 2Подробнее

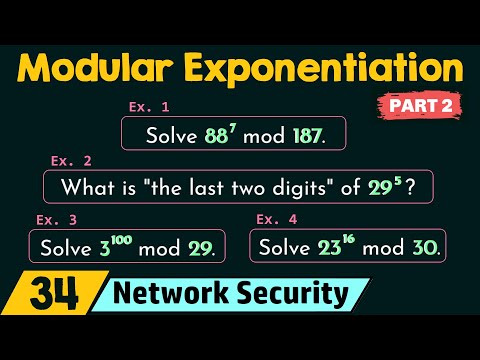
Modular Exponentiation (Part 2)Подробнее
Introduction of Two Fish Algorithm Part 2Подробнее

RSA Encryption Part 2, Computer SecurityПодробнее
