Introduction of Two Fish Algorithm Part 2

Introduction of Two Fish Algorithm Part 1Подробнее

DES ( Data Encryption Standard ) Algorithm Part -1 Explained in Hindi l Network SecurityПодробнее

Introduction to Bayesian data analysis - Part 2: Why use Bayes?Подробнее

Twofish Encryption Visual RecordПодробнее

Twofish MeaningПодробнее

Skipjack, BlowFish, TwoFish, Camilla, XTEAПодробнее

Tutorial 5.2: Tomer Ullman - Church Programming Language Part 2Подробнее

Two-Fish Simulation (Side view)Подробнее

What Is Twofish Algorithm? - Next LVL ProgrammingПодробнее

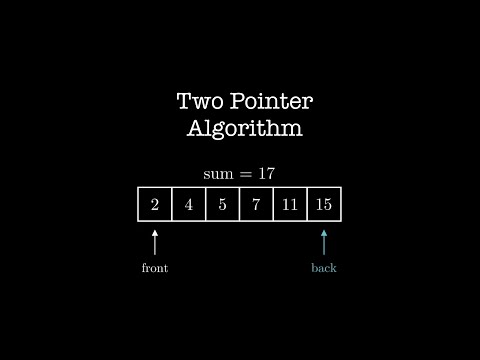
Visual introduction Two Pointer Algorithm | Data Structure and Algorithm for Coding InterviewsПодробнее
CISSP Cyber Security: Encryption Algorithms (Twofish vs Blowfish) #twofish #blowfish #encryptionПодробнее

Blowfish and twofishПодробнее

Twofish vs. Blowfish Explained #securityПодробнее

Encrypt and Decrypt Images Using the Two Fish Algorithm in JavaПодробнее

CSF11903 | NETWORK & SECURITY FUNDAMENTAL ( BLOWFISH / TWOFISH ALGORITHM)Подробнее

Code Review: Twofish implementation in C++ (2 Solutions!!)Подробнее

CEH Cryptography Part 2Подробнее

Greatest Chess Move EverПодробнее

The Twofish Encryption AlgorithmПодробнее

Реализация алгоритмов шифрования семейства twofishПодробнее
