Metasploit Persistence Backdoors Tutorial
Mastering Registry-Based Persistent Backdoor Listeners with Africana-Framework and Metasploit.Подробнее

Creating Persistent Backdoor for Latest Windows by #GICSEHПодробнее

Creating a Persistent Android Payload with Metasploit: TutorialПодробнее
4 simple ways of how bad guys install Backdoor on Windows | Metasploit tutorialПодробнее

HACKING TO DUBBSTEPP [METASPLOIT] Exploitation and uploading a shell for persistenceПодробнее
![HACKING TO DUBBSTEPP [METASPLOIT] Exploitation and uploading a shell for persistence](https://img.youtube.com/vi/RYtuqrxHN-c/0.jpg)
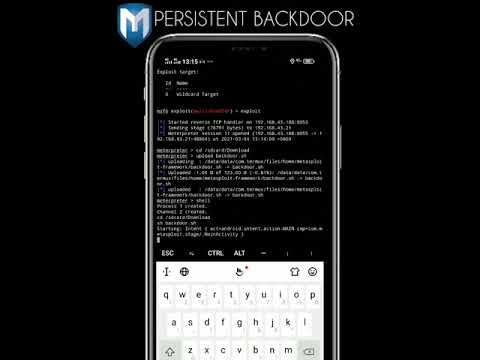
How to Create a Persistent Backdoor in AndroidПодробнее
How to Generate Windows Backdoors with Metasploit FrameworkПодробнее

android backdoor - metasploit backdoor #mobilesecurity #ethicalhackingПодробнее

Android Persistent Backdoor - MetaSploit #metasploit #msfvenom #meterpreter #ethicalhackingПодробнее
Kalıcı Backdoor | Meterpreter Persistent Backdoor | Metasploit Eğitimi 5Подробнее

Penetration Testing with Metasploit: A Comprehensive Tutorial | PT2Подробнее
Hacking windows persistence on metasploit (kali linux) (Do Not Try This On Any PC)Подробнее

Maintaining Access Phase using Metasploit Persistence ModuleПодробнее

Windows Persistence Techniques P2 | Backdoors | TryHackMe Windows Local PersistenceПодробнее

Metasploit Post Modules & Post Exploitation Persistence, Meterpreter Commands & MoreПодробнее
Windows Post Exploitation - Persistence With MetasploitПодробнее

Backdoor Android Devices using msfvenom and metasploit | Hacking TutorialПодробнее

Backdoor Android Devices using msfvenom and metasploit | Hacking Tutorial-2Подробнее

Persistence Backdoor For Android Devices For Continuous SessionПодробнее

Hack Windows System Persistence Backdoor | Reverse shell | Kali Linux tamil | codehuntersПодробнее
