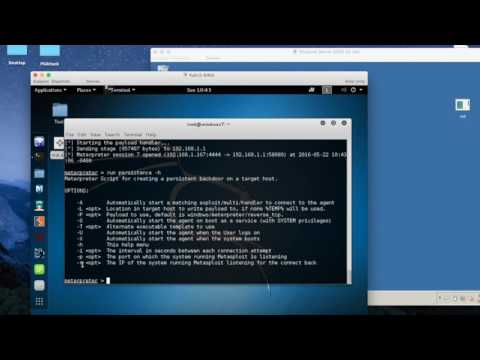
Windows Post Exploitation - Persistence With Metasploit

Creating a Persistent Android Payload with Metasploit: TutorialПодробнее
You need to learn about service injection right now | Persistence on Windows | Post exploitation.Подробнее
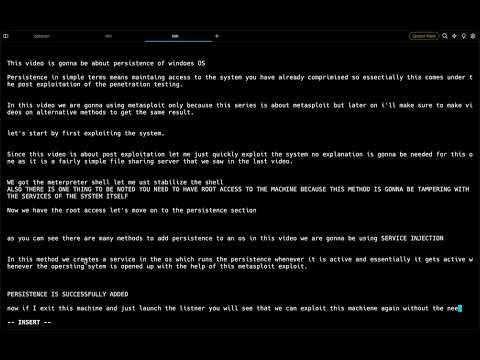
PowerShell Empire | Privilege Escalation & Persistence | Windows 7 Hack LabПодробнее

Android Persistent Backdoor - MetaSploit #metasploit #msfvenom #meterpreter #ethicalhackingПодробнее
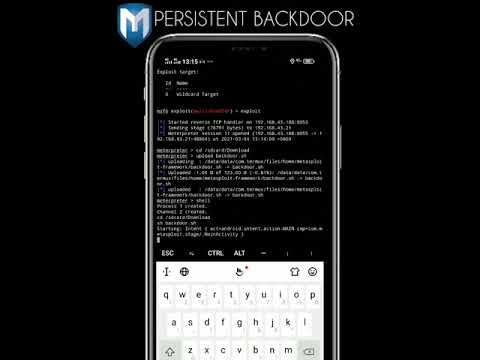
Penetration Testing with Metasploit: A Comprehensive Tutorial | PT2Подробнее
Class 10 Windows Post Exploitation Persistence With MetasploitVideoПодробнее

Class 09 How to Hack Window 10 Privilege Escalation, Post ExploitationПодробнее
Class 07 How to make Payload for All Operating System WebsiteПодробнее

Class 04 How to Use Nmap with MetasploitПодробнее

Class 02 How to Setup lab Environment in VMWare WorkstationПодробнее

Class 03 Some Basic Command of Metasploit frameworkПодробнее

Class #01 Advance Metasploit Hacking Course Intro VideoПодробнее

E3- Empire PowerShell | Persistent Mode - Interaction with MetasploitПодробнее

Hacking windows persistence on metasploit (kali linux) (Do Not Try This On Any PC)Подробнее

Metasploit Post Modules & Post Exploitation Persistence, Meterpreter Commands & MoreПодробнее
DFIR: Hunting for Persistent Malware created with Metrepreter and MetasploitПодробнее

Creating a Cyber Attack – Part 8 (Post Exploitation – Gaining Persistence 2)Подробнее

Hack Windows 7/8/8.1/10 using Metasploit and create PersistentПодробнее

Backdoor with Metasploit - Maintaining PersistenceПодробнее