Introduction to return oriented programming (ROP)
Exploiting a Windows Application Using Return Oriented ProgrammingПодробнее

Part 25 How to Speak with Machine - Return Oriented Programming (ROP) Fundamentals with OllyDbgПодробнее

Netsec Return Oriented Programming 1 - IntroductionПодробнее
Buffer Overflow Explained AppCheck NGПодробнее

Buffer Overflow Explained AppCheck NGПодробнее

ROPing from a Macro Expansion; pwn/smal-arey CakeCTF 2022Подробнее

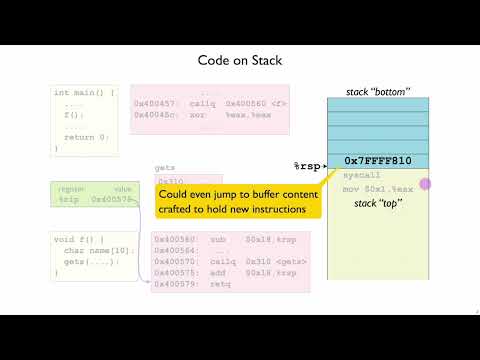
[MemSafety4, Video 9] Return-Oriented Programming OverviewПодробнее
![[MemSafety4, Video 9] Return-Oriented Programming Overview](https://img.youtube.com/vi/_81HHWhHL-A/0.jpg)
Ing. M. Řepa: Introduction to Computer Security (B4M36BSY) – 08 [14. 11. 2024, ZS 24/25]Подробнее
![Ing. M. Řepa: Introduction to Computer Security (B4M36BSY) – 08 [14. 11. 2024, ZS 24/25]](https://img.youtube.com/vi/LEzqI5bSBvU/0.jpg)
Return oriented programming exploitation/ROP gadgetsПодробнее

Return Oriented Programming, an introduction - Patricia Aas - NDC TechTown 2023Подробнее

[Fall 23] Lec07: Return-oriented Programming (ROP)Подробнее
![[Fall 23] Lec07: Return-oriented Programming (ROP)](https://img.youtube.com/vi/lETF9vOj5FI/0.jpg)
Buffer Overflow Explained | P22 | ROP Chains | CTF WalkthroughПодробнее

Return Oriented Shellcode (ROP Shellcode)Подробнее

Intro to Kernel ExploitationПодробнее

Benjamin Kollenda - Embedded Device Exploitation 101: An Introduction to Firmware Hacking emBO++ 23Подробнее

Return Oriented Programming, an introduction - Patricia Aas - NDC Security 2023Подробнее

Return Oriented ShellcodeПодробнее

Can You Build a ROP Chain in Minutes?Подробнее

uint underflow / C++ ROP / libc leak / rop2system - LACTF2023 - pwn/redactПодробнее

Attacking a binary with seccomp/libc leak/ROP open+read+write - DiceCTF 2023 - pwn/bopПодробнее
