Return oriented programming exploitation/ROP gadgets

Exploiting a Windows Application Using Return Oriented ProgrammingПодробнее

Software Exploitation (Undergraduate Level) – Course OverviewПодробнее

First Exploitation Technique - Ret2winПодробнее
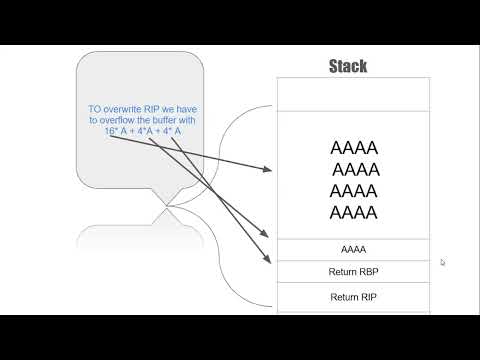
0x03 ROP chain - Binary Exploitation CTF Tutorial | Full Walkthrough (GDB, Pwntools, ROP)Подробнее

buffer underruns dep aslr and improving the exploitationПодробнее

Finding bad characters during exploitationПодробнее

Beginner's Guide to Exploitation on ARM Vol 1Подробнее

Part 25 How to Speak with Machine - Return Oriented Programming (ROP) Fundamentals with OllyDbgПодробнее

SROP Series: Part 2 - Solving HTB Apocolypse 2025 Pwn Challenge - 'Laconic'Подробнее

Syscall: Sigreturn - An SROP Primer (HTB Apocalypse 2025 pwn walkthrough - Laconic Part 1)Подробнее

Binary Exploitation: Ret2Win (CTF Walkthrough)Подробнее

Binary Exploitation Data Execution Prevention MediumПодробнее

Binary Exploitation Data Execution Prevention MediumПодробнее

Demystifying Return Oriented Programming in CybersecurityПодробнее

ROP exploit on a vanilla buffer overflowПодробнее

Ethical Hacking Using Virtual MachinesПодробнее

Exploit Development - Bypass DEP Using VirtualAlloc in a ROP (Return-Oriented Programming) chainsПодробнее

Reverse Engineering Learning - Ret2Shell and ROP GadgetsПодробнее

Software Exploitation, Part 3: DEP/NX exploits, ret2libc and ROP chainsПодробнее
