How to Access Well Known Security.txt file
How to Allow /.well-known/security.txt in .htaccessПодробнее

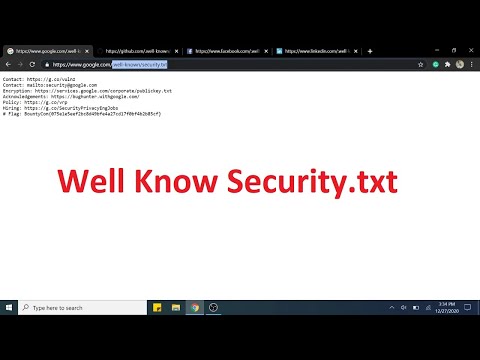
How to Access Well Known Security txt fileПодробнее
What is Security.txt? Does Security.txt Affects SEO?Подробнее
Security.txt: Pros, Cons & Ethical HackingПодробнее

Security.txt demoПодробнее

Security.txt - My Awesome Invention for Security ResearchersПодробнее
