Hacking a Fake NSA Website using PGP Encryption

CYPHERCON11 PISSED Privacy In a Surveillance State Evading Detection Joe CiceroПодробнее

Reports: NSA Cracked, Bypassed Web EncryptionПодробнее

Why the NSA was worried about PGP existing as open source softwareПодробнее

The Complete PGP Encryption Tutorial | Gpg4win & GnuPGПодробнее

How To Use PGP Encryption | gpg4win Kleopatra TutorialПодробнее
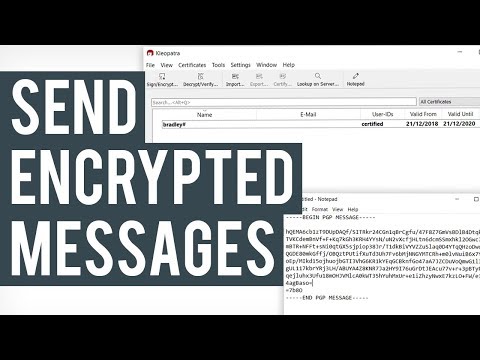
Open Source an Open Invitation to Hack Webmail EncryptionПодробнее

When Cybercriminals with Good OpSec AttackПодробнее

How attackers steal PGP keysПодробнее

Documents Reveal NSA Can Crack Online EncryptionПодробнее

DEF CON 22 - Adrian Crenshaw- Dropping Docs on Darknets: How People Got CaughtПодробнее

Hackers are looking at your websiteПодробнее

Make Advanced Phishing Pages With AI | Bypass Security #chatgpt #cybersecurity #ethicalhackingПодробнее

Ex-NSA hacker tools for real world pentestingПодробнее

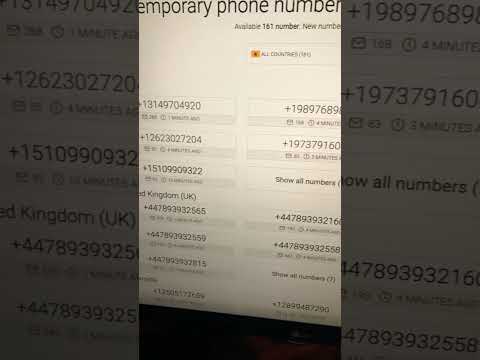
Website you should know about part 10: disposable phone numbers for freeПодробнее
Launch of highly-secure 'cryptophone'Подробнее

How Hackers Clone Websites and Steal Passwords | Real Phishing DemoПодробнее

Hacker #shorts #youtubeshorts #hacker #technology #tech #smartphone #gadgets #chipsПодробнее

Real Hackers Use 'netcat' To Transfer FilesПодробнее

Encryption Basics | CyberSecurityTVПодробнее
