Make Advanced Phishing Pages With AI | Bypass Security #chatgpt #cybersecurity #ethicalhacking

Advanced Phishing with AI & the Last Mile Reassembly Attacks | Bypass Secure Web GatewaysПодробнее

Create a phishing site in 4 minutes?? | Suprisingly easy and convenientПодробнее

How to HACK ChatGPTПодробнее

How To Make Phishing Pages Using Zphisher #cybersecurity #coding #extremehackingПодробнее
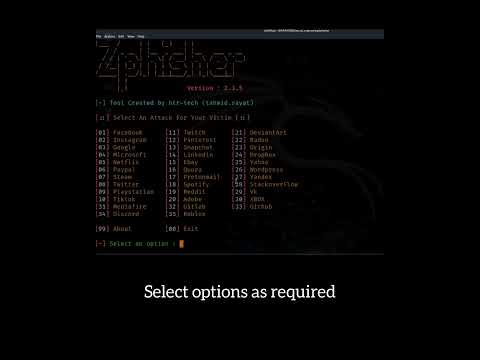
Phishing attacks are SCARY easy to do!! (let me show you!) // FREE Security+ // EP 2Подробнее
Hacking KnowledgeПодробнее

Top Cybersecurity Expert Reveals AI Phishing SecretsПодробнее

How a Hacker Creates a Phishing Website Using AIПодробнее

How Hackers do Phishing Attacks to hack your accountsПодробнее

When you first time install Kali linux for hacking 😄😄 #hacker #shortsПодробнее

Creating a Phishing Website under 28 seconds. #Hacking #Linux #ethicalhacking #cybersecurity #hackerПодробнее

Make your ai essays stealth and beat gptzero easilyПодробнее

Normal people vs programmer vs hackers compression #codingПодробнее
How To Use Chat GPT For Hacking | Methods & BypassesПодробнее

Turnitin AI writing detection bypasserПодробнее

Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее
