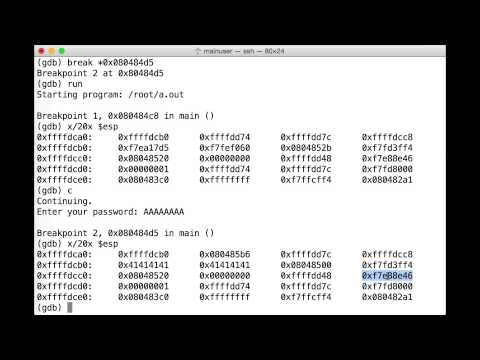
Get Started with GDB and Buffer Overflow Hacking!

CTF | OverTheWire | Wargames | Narnia | Level 2 | Buffer Overflow AttackПодробнее

Buffer Overflows 2/, R2 & gdb - Learning Hacking @ TryHackMe (2024-08-06)Подробнее

Buffer Overflow Hacking Tutorial (Bypass Passwords)Подробнее
SEED Labs: Buffer Overflow Attack (Level 1)Подробнее
How to overwrite return address (Stack Buffer Overflow)Подробнее

Pwntools & GDB for Buffer Overflow w/ Arguments (PicoCTF 2022 #43 'buffer-overflow2')Подробнее
BinExp: buffer overflow return address for gdb and no gdbПодробнее

Overwriting RBP with an Off-by-One Buffer Overflow - Cake - [Intigriti 1337UP LIVE CTF 2022]Подробнее
![Overwriting RBP with an Off-by-One Buffer Overflow - Cake - [Intigriti 1337UP LIVE CTF 2022]](https://img.youtube.com/vi/jU7yB-elFV8/0.jpg)
4: Ret2Win with Function Parameters (x86/x64) - Buffer Overflow - Intro to Binary Exploitation (Pwn)Подробнее

0: Intro/Basics/Setup - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее

Buffer Overflow 101: Ep 3 - Fuzzing the TargetПодробнее
Buffer Overflow attack on a 64-bit ubuntu using gdb-pedaПодробнее

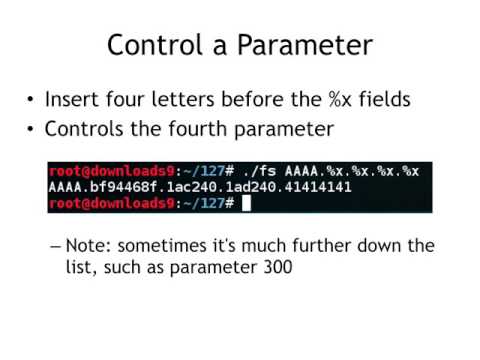
CNIT 127 Ch 4: Introduction to format string bugsПодробнее
Running a Buffer Overflow Attack - ComputerphileПодробнее
How to exploit a buffer overflow vulnerability - PracticalПодробнее
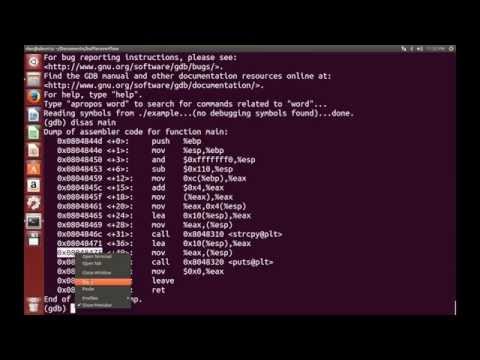
How They Hack: Buffer Overflow & GDB Analysis - James LyneПодробнее