Fileless Malware Analysis & PowerShell Deobfuscation
Fileless Malware Analysis & PowerShell DeobfuscationПодробнее
Finding and Decoding Malicious Powershell Scripts - SANS DFIR Summit 2018Подробнее

Demo 15 - PowerShell DeobfuscationПодробнее

Deobfuscating malicious PowerShell scriptsПодробнее
Decoding Malicious PowerShell ActivityПодробнее

Using PowerDecode +SCDBG to analyze in seconds a fileless PowerShell malwareПодробнее

Powershell Fileless Malware, implementation and DetectionПодробнее

Malware Analysis - DOSfuscation DeobfuscationПодробнее

Powershell Script DeobfuscationПодробнее

How to analyze a malicious powershell script fileless malwareПодробнее
Fileless PowerShell Attack DemoПодробнее

Как работает бесфайловое вредоносное ПОПодробнее

Fileless Malware: How It WorksПодробнее
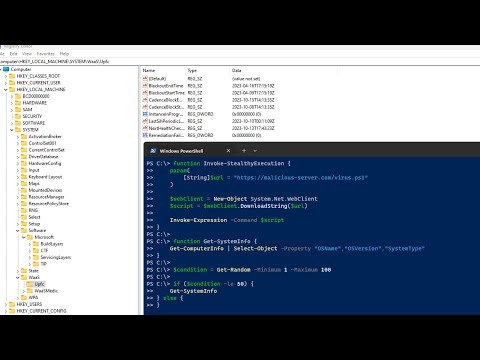
Fileless Ransomware: Powershell NetwalkerПодробнее

Deobfuscate Emotet PowerShellПодробнее

How to Analyze a Malicious Powershell Script & Fileless MalwareПодробнее

PowerDecode in action: Automatic deobfuscation of a malicious PowerShell scriptПодробнее

JScript Deobfuscation - More WSHRAT (Malware Analysis)Подробнее
Demo 17 - Fileless Malware Attack Chain - VBA, WMI, and PowerShellПодробнее
