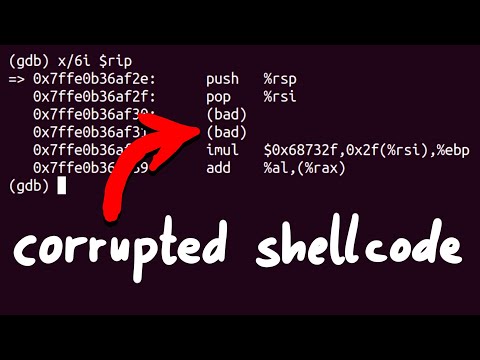
Exploit Dev Pitfall Corrupted Shellcode
9 Generating Shellcode and Getting RootПодробнее
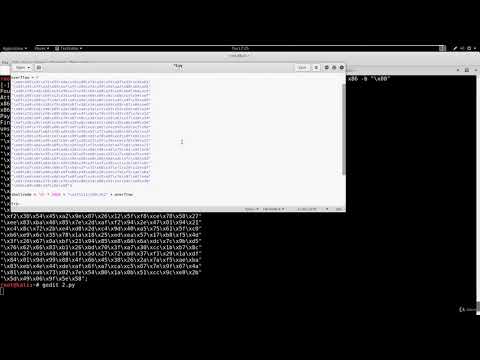
Exploit Fails? Debug Your Shellcode - bin 0x2BПодробнее

First Exploit! Buffer Overflow with Shellcode - bin 0x0EПодробнее
pwn.college - Exploitation Scenarios - Hijacking to ShellcodeПодробнее

F2020 - Binary Exploit MitigationsПодробнее

Exploit Development for Linux (x86) - Using third party shellcodeПодробнее
VULNSERVER Exploit: HTER w/ Assembly & ShellcodeПодробнее
DEF CON 25 - JoSh Pitts - Teaching Old Shellcode New TricksПодробнее
