F2020 - Binary Exploit Mitigations

F2020 intro to binary exploitationПодробнее

binary securities & exploit mitigationsПодробнее

F2020 - Intro to Binary ExploitationПодробнее

Hack The Box - Introduction to Binary Exploitation - Reg - [Walkthrough]Подробнее
![Hack The Box - Introduction to Binary Exploitation - Reg - [Walkthrough]](https://img.youtube.com/vi/72GShSHsRZI/0.jpg)
binary exploitation with buffer overflowПодробнее

Binary Exploitation pwn collegeПодробнее

Binary Exploitation with Buffer Overflow md GitHubПодробнее

#HITBGSEC 2018 D1: File Structures: Another Binary Exploitation Technique - An-Jie Yang (Angelboy)Подробнее

Black Hat USA 2012 - Exploit Mitigation Improvements in Windows 8Подробнее

What modern binary exploitation looks likeПодробнее

Security Summer School v9 - Binary Exploitation Track - Session 12: Bypassing MitigationsПодробнее

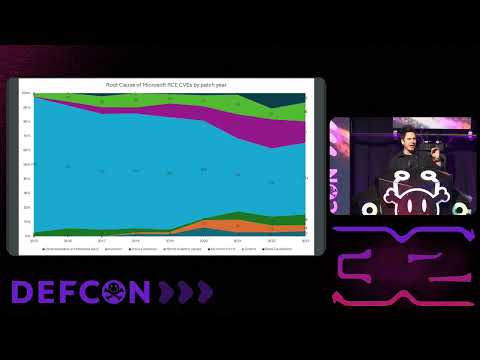
DEF CON 32 - The Rise and Fall of Binary Exploitation - Stephen SimsПодробнее