Buffer Overflow attack - Exploitation and Theory of Vulnerability

Exploiting buffer overflow leads to segfaultПодробнее

Exploiting buffer overflow leads to segfaultПодробнее

Buffer Overflow Attacks - How hackers exploit the vulnerability & How to Mitigate Risks? Explained💥Подробнее

Detail Explain Buffer Overflow AttackПодробнее

Part-1 - Anatomy of a Python Scripted Remote Buffer Overflow w/ Joff ThyerПодробнее

What is a Stack Buffer Overflow? Exploring How To Exploit the StackПодробнее
How to Manually Exploit an Application (Buffer Overflow)Подробнее
Exploiting Return Oriented Programming (ROP) tutorial - Binary Exploitation PWN101Подробнее

How to exploit a buffer overflow vulnerability (security@cambridge screencast)Подробнее

Buffer Overflow | Dear QA | TryhackmeПодробнее

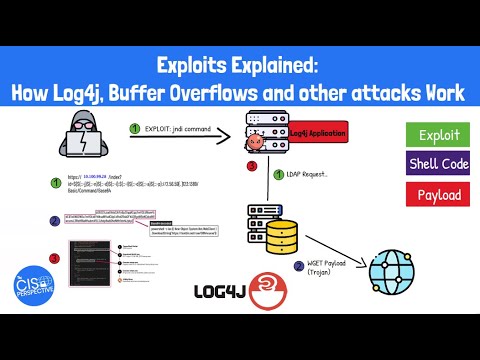
Exploits Explained: How Log4j, Buffer Overflows and Other Exploits WorkПодробнее
Buffer Overflow 101: Ep 1 - x86 Memory FundamentalsПодробнее
Buffer OverflowПодробнее

0x05 - Intro to Stack Buffer Overflow ExploitationПодробнее

Live Buffer Overflow Attack From Windows 10 System | Basic Stack Overflow Explained Complete 10 MinПодробнее
How to exploit a buffer overflow vulnerability | Full PracticalПодробнее

42 Windows Buffer Overflow & Bad chars - OSCP | Offensive Security Certified ProfessionalПодробнее

Type of Cyber Attack- Network Security | DDOS | Buffer OverflowПодробнее

Buffer Overflow Attack Example | Exploiting BinaryПодробнее