Envoy Gateway OIDC Authentication & Authorization Demo
Envoy Gateway OIDC Authentication & Authorization DemoПодробнее

Securing the Gateway: A Deep Dive Into Envoy Gateway's Advanced Security Pol... Huabing (Robin) ZhaoПодробнее

Authentication and Authorization with Istio, Envoy and your IdP of Choice!, Nathan HallПодробнее

Authorization with Envoy at Square - Jelle VanhorenbekeПодробнее

OAuth 2 Explained In Simple TermsПодробнее
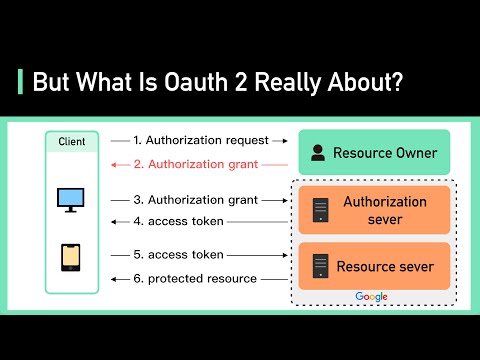
The Key Difference in OIDC: Understanding Access Tokens and ID TokensПодробнее

An Illustrated Guide to OAuth and OpenID ConnectПодробнее

What is Envoy Gateway?Подробнее

How To: OTK Client TestПодробнее

API Authentication with OIDC, Auth0 & TykПодробнее

SAML vs. OpenID (OIDC): What's the Difference?Подробнее

OAuth and OpenID Connect - Know the DifferenceПодробнее
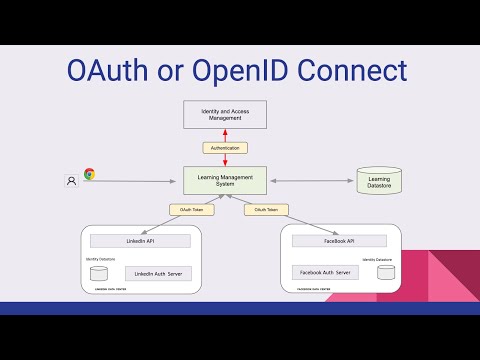
Introduction to OAuth 2.0 and OpenID Connect By Philippe De RyckПодробнее

🔐 OIDC in CI/CD: Secure Your Pipelines! Oauth2.0 #encryptionПодробнее

Keycloak Authentication (Using OpenID) #openid #animation #keycloak #authenticationПодробнее

Okta Authorization Servers for OpenID Connect and OAuth 2.0 IntegrationsПодробнее
Show Code Part 2 | Securing API Workloads Using IDPПодробнее

How To Guide: Compose your own authentication and authorization workflows with Gloo EdgeПодробнее

Envoy Proxy Crash Course, Architecture, L7 & L4 Proxying, HTTP/2, Enabling TLS 1.2/1.3 and moreПодробнее
