Demystifying Identity & Access Management (IAM): SAML, SSO, and Zero Trust Explained for MSPs
Demystifying Identity & Access Management (IAM): SAML, SSO, and Zero Trust Explained for MSPsПодробнее

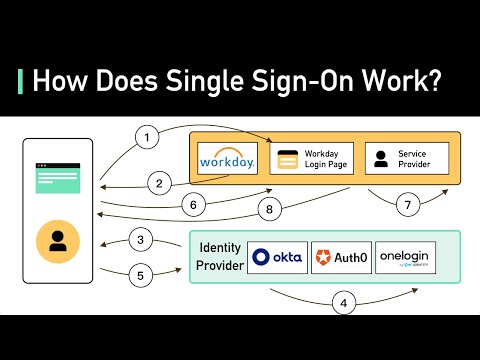
What Is Single Sign-on (SSO)? How It WorksПодробнее
What is single sign on (sso) | How sso works with saml | SAML authentication with AD (2023)Подробнее
Zero TrustПодробнее

What Is IAM? | Identity and Access Management for Beginners (IAM) | IAM for Beginners | SimplilearnПодробнее

Identity & Access Management (IAM)Подробнее

How Identity & Access Management (IAM) powers Threat Protection & Zero TrustПодробнее

The role of identity and access management in Zero Trust SecurityПодробнее

Secure user identities to establish Zero TrustПодробнее

Zero Trust Overview (part 1)Подробнее

Cybersecurity and Zero TrustПодробнее

Zero Trust Access Feature: Single Sign-On (SSO) for SaaS ApplicationsПодробнее

What is SAML? A Comprehensive Guide with ExamplesПодробнее

Evo CEO: ConnectWise Webinar: Identity & Access Management 101 for MSPsПодробнее

Authentication is the first step to Zero TrustПодробнее

Zero Trust Identity Access Management (IAM), Endpoint Detection, Protection and ResponseПодробнее

ZT2.0: M1T5: Applying Zero Trust Principles to a SaaS applicationПодробнее

Roles and Identity Access ManagementПодробнее
