C# Encrypt And Decrypt - Part 2 (Tutorial)

Security+ Crash Course SY0-701 - Domain 1.0 Part 2Подробнее

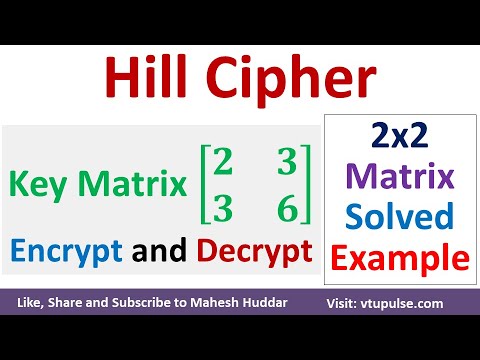
1. Hill Cipher Solved Example 2x2 Key Matrix | Hill Cipher Encryption and Decryption Mahesh HuddarПодробнее
ENCRYPT and DECRYPT a STRING in C# - PART TWOПодробнее
ENCRYPT and DECRYPT a STRING in C# - PART ONEПодробнее
Sentence converted secret code through (decrypt) in c language part 2, (encrypt video part 1)Подробнее

Playfair Cipher (Part 1)Подробнее

Caesar Cipher (Part 1)Подробнее

Cryptography Full Course Part 1Подробнее

Cyber Security Basics | Lesson #7 | Playfair Cipher Code - Part 2 | Coding Blocks JuniorПодробнее

F2020 - Modern Cryptography: Part 2Подробнее

Cryptography Encrypt and Decrypt by C# Part 2Подробнее

CSV file Update| Delete | Encryption | Decryption | C# | Part - 2Подробнее

Playfair Cipher Encryption / Decryption code -part 2- بالعربيПодробнее

Monoalphabetic Cipher Decryption Part 2Подробнее

Flowgorithm - Caesar Cipher Part 2 - DecryptionПодробнее

Unicode Substitution Cipher Part 2Подробнее

C# How To Program 5.41: Enforcing Privacy with Cryptography PART 2: Inheritance, MethodsПодробнее

Safest Login Form in C# with AES Encryption & Decryption Tutorial Part 2Подробнее

Public Keys Part 2 - RSA Encryption and DecryptionsПодробнее
