Public Keys Part 2 - RSA Encryption and Decryptions
CSS Video 27 Part 2: RSA Additional exercise of Encryption & Decryption, CRT, Multiplicative InverseПодробнее

Wireshark 101 THM Part 2 (http & https) Decrypt with RSA keyПодробнее

RSA algorithm | Decryption key | Cyber security | p=3 , q= 5, e=3 , m= 8Подробнее

Mastering RSA Encryption and Decryption: A Step-by-Step Guide Part 2Подробнее

Part 2- How do prime numbers play a key role in protecting your data?#mathematics #maths #sat #techПодробнее

Signing and Validating JWT Token Using RSA public and private key in ASP.NET Web API with C# -Part 4Подробнее

1.7.5 Playfair Cipher Part 2 in TamilПодробнее

Decrypt RSA-encrypted password - Basilic CTF Ep4Подробнее

Basics of Cryptology – Part 23 (Cryptography – Modern Hybrid Encryption)Подробнее

RSA Asymmetric Encryption & Decryption Code 2Подробнее

Part 2: What is KMS in GCP ? Create a asymmetric encryption in GCP .#gcp #asymmetric keyПодробнее

9 RSA Encryption AlgorithmПодробнее

RSA Algorithm - Explained with Examples - Cyber Security - CSE4003Подробнее
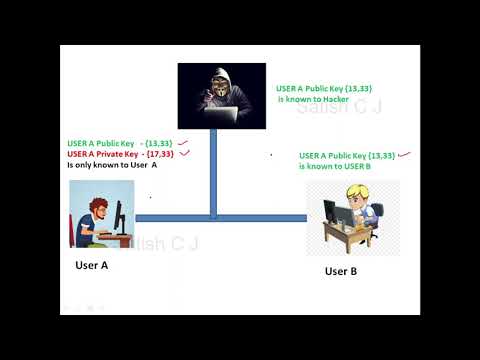
Encryption/Cryptography Basics Part 2Подробнее

How to Encrypt with RSA (but easy)Подробнее

Cryptography Full Course Part 2Подробнее

Cryptography Full Course Part 1Подробнее

How RSA Encryption WorksПодробнее
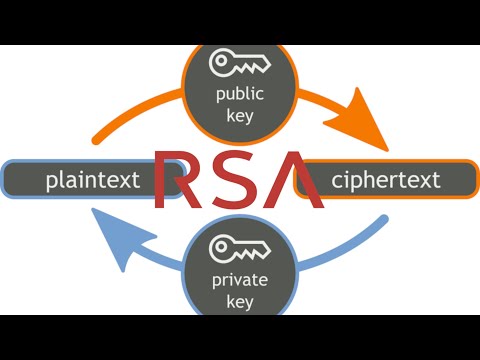
Break (Reduced) RSA Using FactorizationПодробнее

Threshold RSA: Splitting the private decryption key - Part 2Подробнее
