How to exploit a buffer overflow vulnerability | Full Practical
System Hacking : Buffer Overflow , Privilege Escalation & Maintaining Access Made EasyПодробнее
How to Exploit a Buffer Overflow to Bypass Username Validation in C CodeПодробнее

How Overflow Exploits Can Be Carried Out: A Practical ExampleПодробнее

Hacker Course Buffer Overflow A Practical Example with ExploitПодробнее
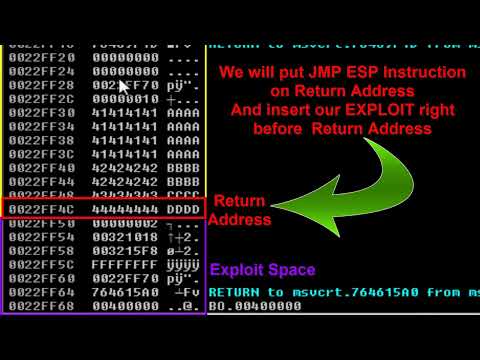
Buffer Overflow | tryhackme | Practical | Part-04 | CrifoxulПодробнее

Buffer Overflow | tryhackme | Practical | Part-02 | CrifoxulПодробнее

Buffer Overflow | tryhackme | Practical | Part-01 | CrifoxulПодробнее

Buffer Overflow Explained With PracticalПодробнее

Linux Buffer Overflow - Exploit Development 9Подробнее

Defending Against Buffer Overflow Attacks: Expert Insights #cybersecurity #bufferoverflowПодробнее

What is Buffer Overflow Attack and Practical in #hindi #englishПодробнее
Cyber Security How can an attacker exploit a buffer overflow vulnerabilityПодробнее

Buffer Overflow - SPIKING!Подробнее
buffer overflow 0- picoCTF practice challenges { Binary Exploitation }Подробнее
buffer overflow 1- picoCTF practice challenges { Binary Exploitation }Подробнее
clutter overflow - picoCTF practice challenges { Binary Exploitation }Подробнее

Exploiting Return Oriented Programming (ROP) tutorial - Binary Exploitation PWN101Подробнее

A Beginner's Guide to Buffer Overflow | Step By Step | Craw Security #bufferoverflow #hackingПодробнее

OSCP-Style Buffer Overflow - Sync Breeze 10.0.28Подробнее
3: Return to Win (Ret2Win) - Buffer Overflows - Intro to Binary Exploitation (Pwn)Подробнее
