AES-ECB Cryptography - Breaking Encryption Without a Key
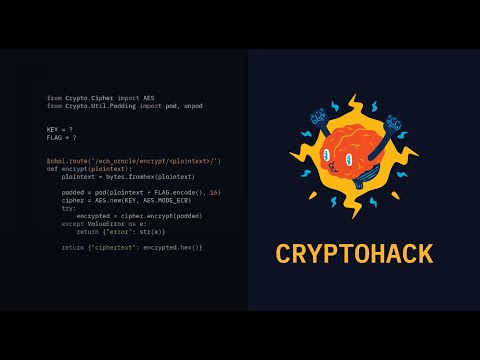
aes ecb cryptography breaking encryption without a keyПодробнее

Breaking AES with side channel analysis - Turid Herland - NDC Security 2022Подробнее

Ron Bowes, Reversing Crypto the Easy Way | KringleCon 2019Подробнее

Chapter 02Подробнее

All-Army CyberStakes! AES-ECB Plaintext RecoveryПодробнее

How can you attack an ECB cipher? [Capture The Flag Fundamentals]Подробнее
![How can you attack an ECB cipher? [Capture The Flag Fundamentals]](https://img.youtube.com/vi/unn09JYIjOI/0.jpg)
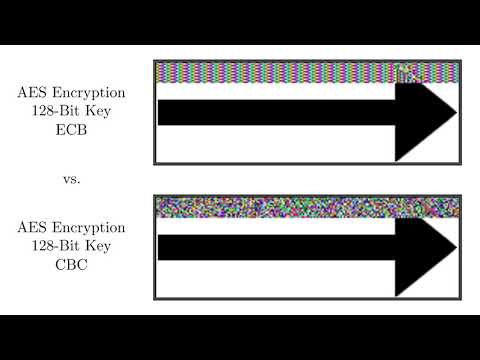
AES Encryption (ECB vs. CBC) VisualizationПодробнее
Brute Forcing AES-ECB with Emoji [Hackvent 2022 - Day 20]Подробнее
![Brute Forcing AES-ECB with Emoji [Hackvent 2022 - Day 20]](https://img.youtube.com/vi/sSZOP9pKc3Q/0.jpg)
C 201 Cracking AESПодробнее
AES Explained (Advanced Encryption Standard) - ComputerphileПодробнее

Break RSA Encryption in 10 Lines of Python Code | #Shorts Quantum Computing with Shor's AlgorithmПодробнее
Electronic Codebook (ECB)Подробнее

Applied Cryptography: 4. Block ciphers (AES)Подробнее

Modes of Operation - ComputerphileПодробнее

Encryption EXPLAINED in 30 seconds👩💻 #technology #programming #software #tech #computerscienceПодробнее

CryptoPals Challenge 7 - AES in ECB mode (C++)Подробнее

Breaking Ciphers - Picking The Locks of Cryptographic Keys | University LectureПодробнее

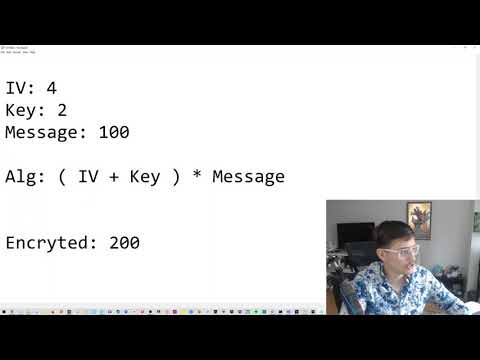
AES Encryption: What's the difference between the IV and Key? Why do we need an IV?Подробнее
Computer Hacking - Cryptopals 3/n (More repeating key XOR cipher, some AES)Подробнее

ECB - Electronic code book (encryption) | information security #studyshorts #studyeasierbypoojapatelПодробнее

What is encryption?Подробнее

All-Army CyberStakes! AES-ECB Plaintext RecoveryПодробнее
