Zero Trust and Secure Access without Losing Visibility

Menlo Secure Application Access & Browsing Forensics - security & visibilityПодробнее

Trend Vision One™ Zero Trust Secure Access | GenAl security simplifiedПодробнее

A closer look at Microsoft Entra Internet AccessПодробнее

Give Me 5 - Episodio 7 - Vision One Zero Trust Secure Access – Private Access workflowПодробнее

Give Me 5 - Episodio 5 - Vision One Zero Trust Secure Access – Internet Access workflowПодробнее

Trend Vision One™ Webinars – ASRM y Zero Trust Secure Access (Sesión 2)Подробнее

Identity Zero-Trust: From Vision to Practical ImplementationПодробнее

Webinar ZeroTrust - Vision Secure AccessПодробнее

Trend Micro Vision One - Zero Trust Secure AccessПодробнее

Stay Protected with Zero Trust Network Access and AWS | InstasafeПодробнее

Duo + Meraki - Simplify Secure AccessПодробнее

VMware Strategy for Intrinsic Security and Zero TrustПодробнее

#SANS Webinar Zero Trust: From Vision to ExecutionПодробнее

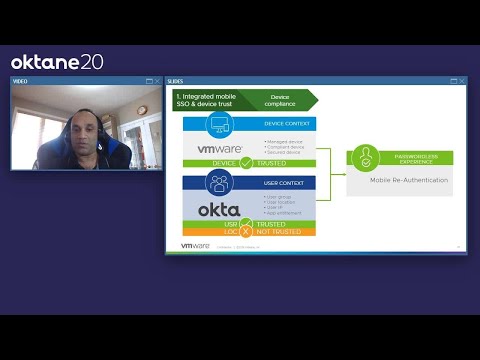
Okta + Workspace ONE: Secure access for the Remote WorkforceПодробнее