What is HMAC? | Simple Explanation + Uses + Interview Q&A
HMAC explained | keyed hash message authentication codeПодробнее

MAC / HMAC - Message Authentication Code / Hash Bashed Message Authentication CodesПодробнее

Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - CryptographyПодробнее

Securing Stream Ciphers (HMAC) - ComputerphileПодробнее

HMAC & Message Authentication Codes (MACs) - Why Hashing alone is NOT ENOUGH for data integrityПодробнее
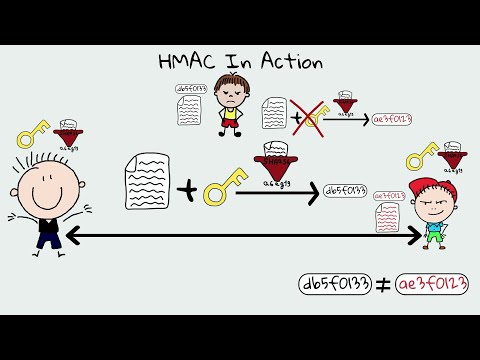
#36 HMAC (Hash Based) & CMAC (Cipher Based) |CNS|Подробнее

HMAC Explained - Message Authenticity and IntegrityПодробнее

Cryptography Basics: HMAC ValidationПодробнее

HMAC SecurityПодробнее

Can HMAC Be Used With Different Hash Functions? - CryptoBasics360.comПодробнее

CMAC or HMAC?Подробнее

HMAC vs digital signatureПодробнее

MAC Based on Hash Function | HMAC in network securityПодробнее

HMAC - Hash-based Message Authentication CodeПодробнее

Understanding How HMAC SHA-256 WorksПодробнее

Hash Based Message AuthenticationПодробнее

Part 6: Security and Authentication - Virtual Mock Backend InterviewПодробнее

How Does HMAC Provide Message Authentication? - SecurityFirstCorp.comПодробнее

25-HMAC-Hashing Based Message Authentication CodeПодробнее

API testing interview questions and answers for QA EngineersПодробнее
