Weak file permissions Linux Privilege Escalation | Fortify Solutions ethical hacking cyber security

How 2 Perform Privilege Escalation in Linux & various methods - From User 2 Root - Real World Demo🔓Подробнее

Weak File Permissions || Linux Privilege EscalationПодробнее

TryHackMe! Linux Privilege Escalation - Weak File Permissions - OSCP TrainingПодробнее

Linux Privilege Escalation for BeginnersПодробнее

Linux Privilege Escalation 2024 | C 5/29 | Linux File Permissions | PentestHintПодробнее

Binary Exploitation vs. Web SecurityПодробнее

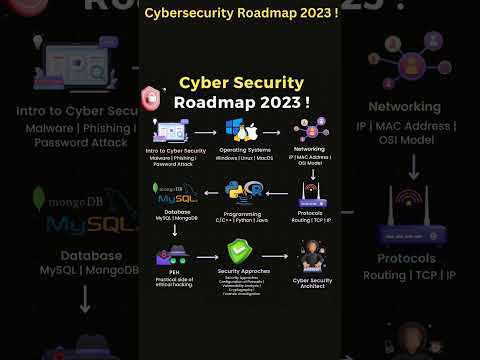
Cybersecurity Roadmap 2023 ! #cybersecurityПодробнее
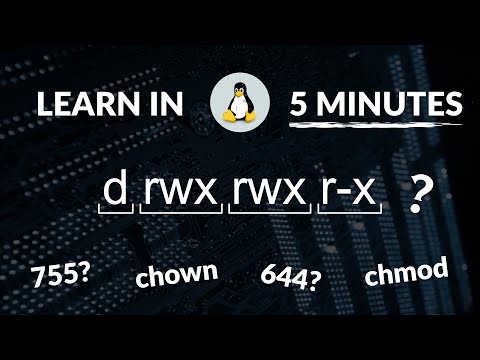
Linux File Permissions in 5 Minutes | MUST Know!Подробнее
OSCP Linux Privilege Escalation (Weak File Permissions - Writable /etc/shadow)Подробнее

How Hackers Gain Root Access | Linux Privilege EscalationПодробнее

Linux Privilege Escalation Through Misconfigured File Permissions - Cyberseclabs LeakageПодробнее

SQL Injection 101: Exploiting VulnerabilitiesПодробнее

A Day in the Life of Cyber Security | SOC Analyst | Penetration Tester | Cyber Security TrainingПодробнее

Hacking Linux // Linux Privilege escalation // Featuring HackerSploitПодробнее
Hacking KnowledgeПодробнее
