Understanding Blind SQL Injection Vulnerability: Detection and Mitigation Strategies

61 Data Extraction: Mastering Time-Based Blind SQL Injection TechniquesПодробнее

60. Time-Based Blind SQL Injection: A Deep Dive into Stealthy Exploitation TechniquesПодробнее

56. Exploring Blind SQL Injections for Ethical HackingПодробнее

Vulnerability Report: SQL Injection Analysis and MitigationПодробнее

Understanding Blind SQL Injection and Strengthening Your DefensesПодробнее
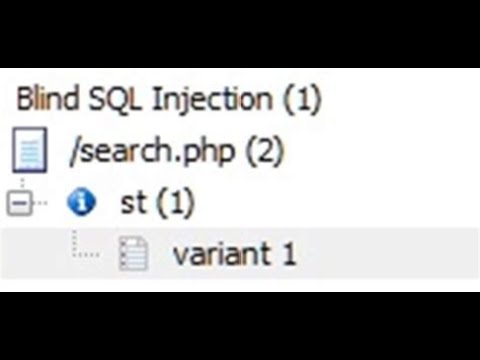
💻 Blind SQL Injection ExplainedПодробнее

Database Breached: The Power of SQL InjectionПодробнее
SQL Injections are scary!! (hacking tutorial for beginners)Подробнее

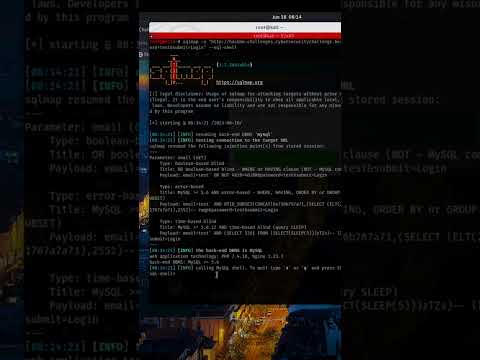
Find SQL Injection vulnerability with sqlmapПодробнее
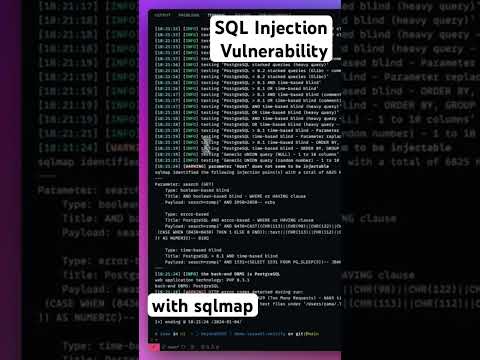
What Is SQL Injection?Подробнее
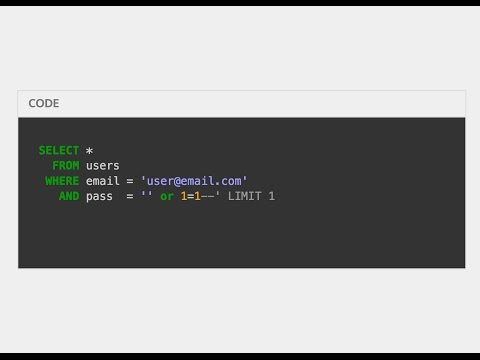
SQL injection Union attack & Blind SQL injection #sql #blog #mediumПодробнее
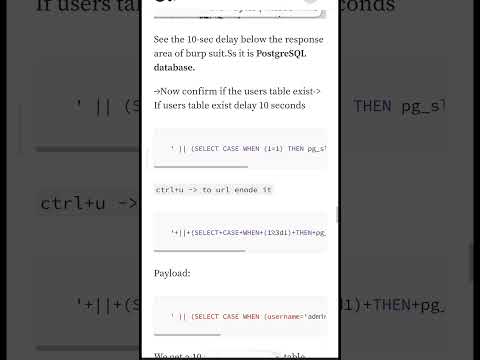
Blind SQL Injection Made EasyПодробнее
What Is Blind SQL Injection? Understanding the VulnerabilityПодробнее

What is Blind SQL Injection? #BlindSQLInjection #shortsПодробнее

SQL injection vulnerability allowing login bypassПодробнее
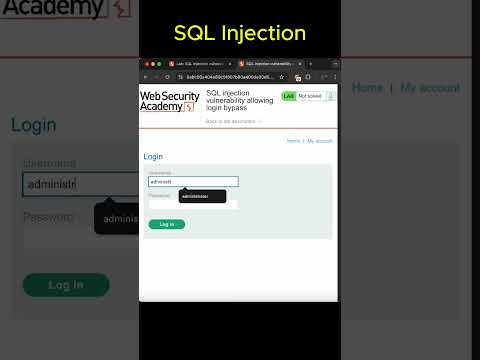
41. Discovering & Exploiting Blind SQL InjectionsПодробнее

SQL Injection Lab 2 - SQL injection vulnerability allowing login bypassПодробнее
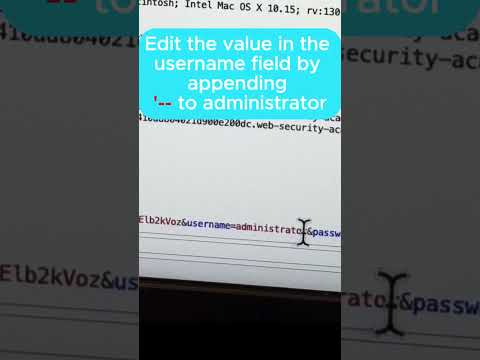
Exploring SQL Injection Attacks😈SQL injection in termuxПодробнее
Guarding Against SQL Injection: Detection and Mitigation TacticsПодробнее

4 Tips to Prevent Blind SQL Injection AttacksПодробнее
