(Template/Example) Introduction to our InfoSec Program

ISO 27001:2022 Implementation: From Start to Finish with Case StudyПодробнее

"Unlock the Secret to Building the Perfect Risk Management Plan"Подробнее
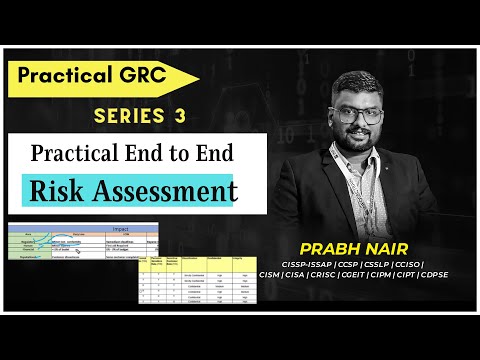
How to Draft Information Security Strategy for an Organization: Step by StepПодробнее

A Day in the Life of Cyber Security | SOC Analyst | Penetration Tester | Cyber Security TrainingПодробнее

Brief Explanation of cyber crime and its Types #cybercrime #typesПодробнее

How To Become a CISSPПодробнее

Introduction to Information Security | Security 1Подробнее

BEST Way To Approach Technical InterviewsПодробнее

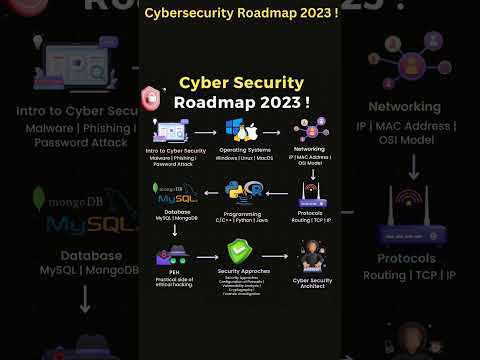
Cybersecurity Roadmap 2023 ! #cybersecurityПодробнее
Building a Cybersecurity FrameworkПодробнее

Explore SailPoint: Identity Governance Demo & Career GuideПодробнее

Cybersecurity Roadmap in 2025 | Top Certifications, Salary Trends & Future ScopeПодробнее
Building the information security industry model - Information Security: Context and IntroductionПодробнее

4 Entry Level Cyber Security Jobs - No experience needed #ShortsПодробнее

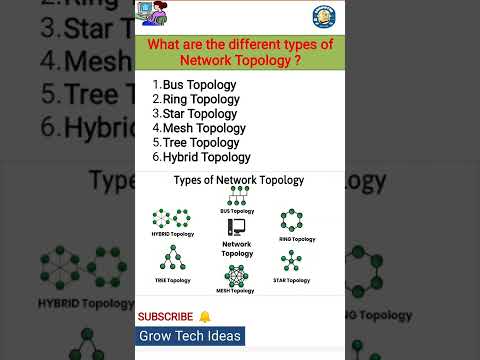
What are the different types of Network Topology ? 6 Types of Topology in Computer NetworkingПодробнее
Information Security Awareness Employee Training: Protect Your Company's Data and ReputationПодробнее

How to introduce yourself as an experienced prof in an interview #interviewtips #introduceyourselfПодробнее
Most Useless Degree? #shortsПодробнее

Cybersecurity for Beginners: Basic SkillsПодробнее
I did 100s of Cyber Security interviews and I learned thisПодробнее
An Introduction to Cybersecurity CareersПодробнее

Advice for Beginners in Cyber SecurityПодробнее
