Software Security [Fall 2023 W4 - Buffer Overflow]
![Software Security [Fall 2023 W4 - Buffer Overflow]](https://img.youtube.com/vi/72pmfO0WYNc/0.jpg)
Software Security [Fall 2023 W3 - Background and Buffer Overflow]Подробнее
![Software Security [Fall 2023 W3 - Background and Buffer Overflow]](https://img.youtube.com/vi/WgCycH3k-oQ/0.jpg)
Buffer overflow 2 [Software Security - Fall 2022 - Week4]Подробнее
![Buffer overflow 2 [Software Security - Fall 2022 - Week4]](https://img.youtube.com/vi/s4_vORfZKGM/0.jpg)
Software Security [Fall 2023 W5 - Buffer Overflow]Подробнее
![Software Security [Fall 2023 W5 - Buffer Overflow]](https://img.youtube.com/vi/jpDvEzPcq_s/0.jpg)
Software Security: Vulnerabilities - Integer/Buffer OverflowПодробнее

Buffer overflow 1 [Software Security - Fall 2022 - Week3]Подробнее
![Buffer overflow 1 [Software Security - Fall 2022 - Week3]](https://img.youtube.com/vi/LNlgt7t5Xzg/0.jpg)
Buffer overflow 3 [Software Security - Fall 2022 - Week5]Подробнее
![Buffer overflow 3 [Software Security - Fall 2022 - Week5]](https://img.youtube.com/vi/FlFVEOiUpwU/0.jpg)
Buffer overflow 4 frame pointer attack [Software Security - Fall 2022 - Week6]Подробнее
![Buffer overflow 4 frame pointer attack [Software Security - Fall 2022 - Week6]](https://img.youtube.com/vi/TSgLw63MQ0k/0.jpg)
Buffer OverflowПодробнее

Binary Exploitation vs. Web SecurityПодробнее

Apple iOS, iPad OS, MacOS, VisionOS: buffer overflow (CVE-2024-27851) #shorts #breakingПодробнее

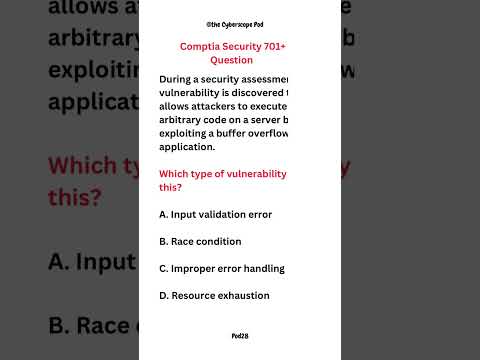
CompTIA Security+ (SY0-701) Question: Buffer Overflow VulnerabilityПодробнее
GStreamer: GStreamer AV1 Video Parsing Stack-based Buffer Overflow (CVE-2024-0444) #shorts #breakingПодробнее

Buffer Overflow - OpenluckПодробнее
The Dangers of Buffer Overflow Exploits 💀#shorts #hacker #securityПодробнее
Google Chrome: Heap buffer overflow in WebAudio (CVE-2024-4559) #shorts #breakingПодробнее
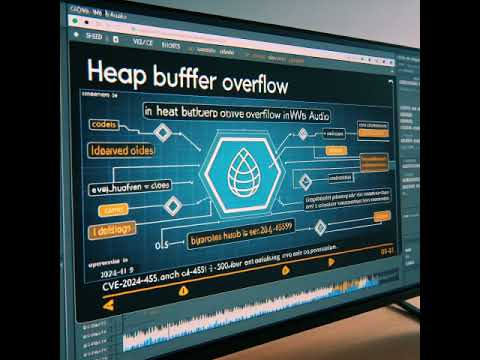
Ivanti products: stack-based buffer overflow (CVE-2025-0283) #shortsПодробнее

Vulnerability vs Exploit | Difference between both | Explained in #shorts - 259 💥Подробнее
Атака переполнения буфера, объясненная в кибербезопасностиПодробнее