SEH Exploits Tutorial - Part six

SEH overflow part 1 ~ Exploit developmentПодробнее
CNIT 127 Ch 8: Windows overflows (Part 1)Подробнее
Exploit Research Megaprimer Part 6 Seh BasicsПодробнее

SEH Exploits Part 1Подробнее
SEH exploit tutorialПодробнее

Exploits - Part 1.movПодробнее

SEH Exploits Tutorial - Part fourПодробнее

SEH Exploits Tutorial - Part fiveПодробнее

Buffer Overflow Tutorial - Part 6Подробнее
OpenSecurityTraining: Introduction To Software Exploits (day 1, part 6)Подробнее

Buffer Overflow Primer Part 6 Exploiting a ProgramПодробнее
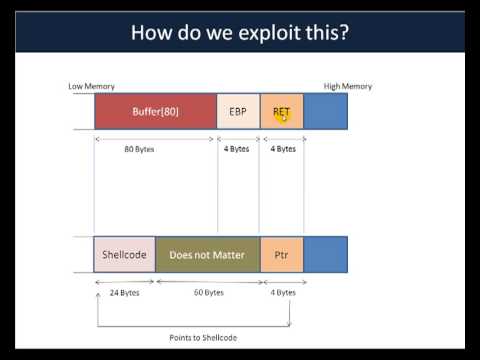
Exploits - Part 2 2.movПодробнее

SEH Exploiting by Amir Reza TavakolianПодробнее

Exploits - Part 4 2.movПодробнее

👨💻 Exploit Development Part 6 - Writing A ROP DecoderПодробнее

Exploits, Part 3Подробнее

Exploit Development v4: SEH (Structured Exception Handler) Exploitation: Soritong MP3 PlayerПодробнее

Exploits - Part 2 - 1.movПодробнее

General Technique for SEH ExploitsПодробнее

Exploits Part 3 1.movПодробнее
