Security - Users and Roles
AWS Devops | IAM | Identity Access Management | IAM user | Groups | Roles & Policies | Session 49 |Подробнее
Create and Manage User Roles in Entra IDПодробнее

Create a Role Hierarchy of Data Security in Trailhead Salesforce 2025!Подробнее

Top Spring Security Interview Questions & Answers | Spring Boot | Authentication Authorization RoleПодробнее
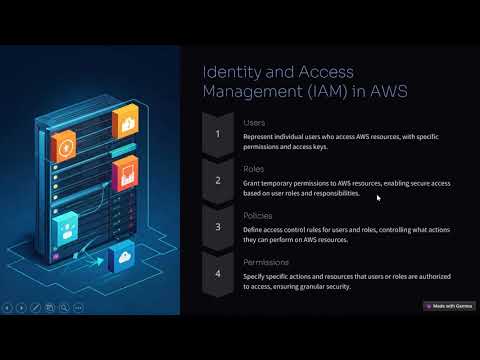
AWS IAM: Users, Groups, Roles, and Policies - Comprehensive Guide for Beginners #awsiam #iam #awsПодробнее

Spring Security Role-based Authorization Spring Boot 3 + RestAPI + JPA + MySQL using STSПодробнее

One Identity Active Roles: Fortify your identity security journeyПодробнее

New Client Security Admin User RoleПодробнее

User /Roles / Security and permission in Access level in VMПодробнее

Key Security Roles Administrators, Users, and OwnersПодробнее

6-SECURITY CONTROL ACCESS DATA-USER ROLE-ACCOUNTANTПодробнее

5- SECURITY CONTROL DATA ACCESS BY USER ROLE DATA ENTRY 2Подробнее

4-SECURITY CONTROL-DATA ACCESS USING DATA ENTRY 1 USER ROLEПодробнее

3- SECURITY CONTROL USER NAMES AND PASSWORDS FOR USER ROLESПодробнее

2-SECURITY CONTROL -USER ROLES IN TALLY PRIMEПодробнее

How to Manage WordPress User Roles for Better Security and EfficiencyПодробнее

ROLES y RENOVAR JWT con SPRING SECURITY: La SEGURIDAD DEFINITIVAПодробнее

Dataverse Role Security | Basic Visual Explanation With ExamplesПодробнее

Extract Security Role & Privileges for logged in user using Power Apps JavaScript (model driven app)Подробнее

How to get User Security Role in Power Apps | Check User AccessПодробнее
