RSAC TV: The Rise of Supply Chain Attacks

The Future of Supply Chain Security | RSAC 2020Подробнее

The Rise of Malware Within the Software Supply ChainПодробнее
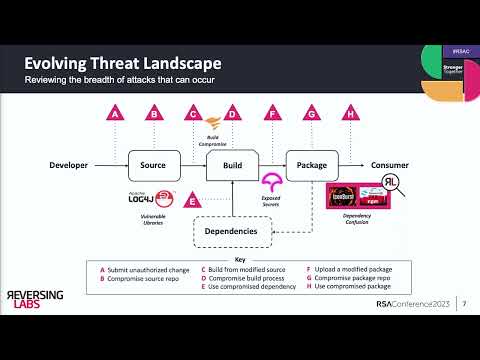
Insights into New Supply Chain and Cloud-Identity AttacksПодробнее

What Hacking the Planet Taught Us About Defending Supply Chain AttacksПодробнее

RSAC 365 Virtual Seminar: Supply Chain Security (Part 2)Подробнее

Shine a Spotlight - Rise of Supply Chain AttacksПодробнее

Lessons Learned from the Summer of Supply Chain AttacksПодробнее

The Simple, Yet Lethal, Anatomy of a Software Supply Chain AttackПодробнее

The Supply Chain ThreatПодробнее

RSAC 2021 Keynote: A Resilient JourneyПодробнее

Chronicle of the Supply Chain Attack and Two Attack StrategiesПодробнее

RSAC 365 Virtual Seminar: Supply Chain Security (Part 1)Подробнее

Episode 1, The Rise of Software Supply Chain AttacksПодробнее

Supply Chain Attacks: Full Geopolitical Risks Webinar on Supply Chain Attacks (Digital & Physical)Подробнее

Exploiting Vulnerabilities and Flaws to Attack Supply ChainПодробнее

Linked-Out: Security Principles to Break Software Supply Chain AttacksПодробнее

Quick Look: Taking Control of Cyber-Supply Chain SecurityПодробнее
