RSA Asymmetric Algorithm
RSA Cryptography Song (Asymmetric-key Algorithms) (Public-key Encryption)Подробнее

RSA - Asymmetric Cryptographic AlgorithmПодробнее

Information Security | Cryptography | Asymmetric Encryption | RSA AlgorithmПодробнее

CSS Video 27 (Part1) :RSA Asymmetric/Public Cryptographic Encryption, Decryption,, e,d,n,p,q,CRTПодробнее

Encryption Explained: Symmetric vs Asymmetric Algorithms for Network SecurityПодробнее

Unit 4 Asymmetric Key Algorithm ▶️Cryptography and Network Security #makaut #ai#cryptography#networkПодробнее

Introduction to Asymmetric Cryptography - Euler's Theorem & RSA ProofПодробнее
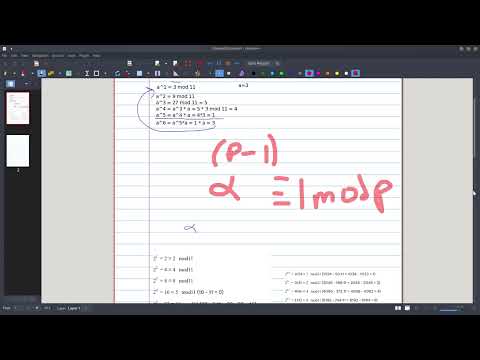
RSA Cryptosystem ||Asymmetric Cryptosystem || Public Key Cryptography || Cryptography & Network SecПодробнее

Asymmetric algorithmПодробнее

Implementing Asymmetric Encryption in Python with RSAПодробнее

008 Asymmetric Cryptography RSA PGP GPG ECC Quantum Computing TOR PFSПодробнее

Data Manipulation (Encryption) #privatekey #publickey #rsa #aes #decryption #symmetric #asymmetricПодробнее

RSA algorithm | Decryption key | Cyber security | p=3 , q= 5, e=3 , m= 8Подробнее

RSA Algorithm in Tamil | Cryptography and Cyber Security in Tamil | CB3491 Lectures in Tamil Unit 4Подробнее

Cryptography Asymmetric encryption RSA algorithmПодробнее

RSA Key Exchange and Forward Secrecy - Cryptography EssentialsПодробнее

The RSA Encryption Algorithm - How Does It Actually Work + Step-by-Step Example.Подробнее
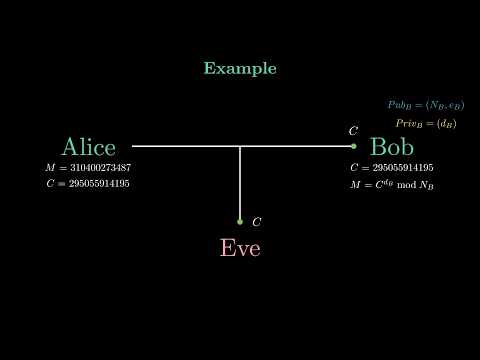
Cryptography Asymmetric Public key Cryptography RSA algorithmПодробнее

RSA & Asymmetric Encryption - Cryptography EssentialsПодробнее

Presentation of Implementation of Asymmetric Encryption with 2048-bit RSA AlgorithmПодробнее
